easychallenge
下载附件,得到一个pyc文件
有关pyc文件的介绍
那么我们反编译一下看看它的源码是什么
在线反编译
得到以下代码:
#! /usr/bin/env python 2.7 (62211)
#coding=utf-8
# Compiled at: 2018-08-08 22:29:44
#Powered by BugScaner
#http://tools.bugscaner.com/
#如果觉得不错,请分享给你朋友使用吧!
import base64
def encode1(ans):
s = ''
for i in ans:
x = ord(i) ^ 36
x = x + 25
s += chr(x)
return s
def encode2(ans):
s = ''
for i in ans:
x = ord(i) + 36
x = x ^ 36
s += chr(x)
return s
def encode3(ans):
return base64.b32encode(ans)
flag = ' '
print 'Please Input your flag:'
flag = raw_input()
final = 'UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E==='
if encode3(encode2(encode1(flag))) == final:
print 'correct'
else:
print 'wrong'
发现flag经过encode1、encode2、encode3,后,只要与final相等,则会输出correct,所以只需将整个函数过程逆向进行一遍,就能得到flag,代码如下。
import base64
def decode1(ans):
s=''
for i in ans:
x=ord(i)-25
x=chr(x^36)
s+=x
return s
def decode2(ans):
s=''
for i in ans:
x=i //在这里不用再使用ord()了,因为base32decode输出的是int
x=x ^ 36
x=chr(x-36)
s+=x
return s
def decode3(ans):
return base64.b32decode(ans)
final='UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E==='
flag=decode1(decode2(decode3(final)))
print(flag)
转轮机加密
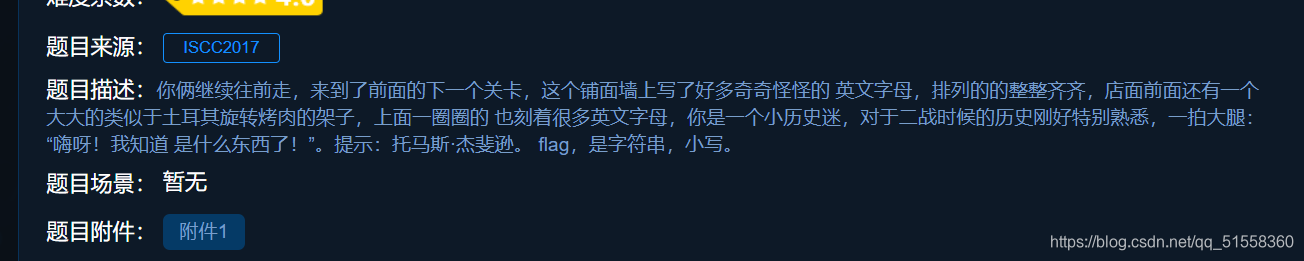
打开附件,内容为:
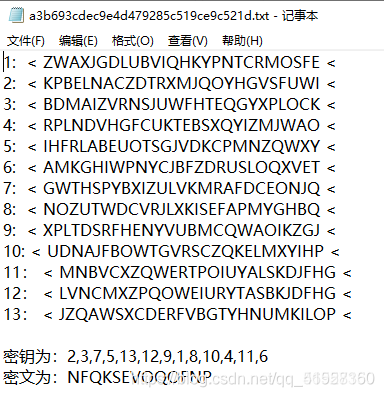
根据密钥提示,将第二行换到第一行,以此类推,第六行换到第十三行。
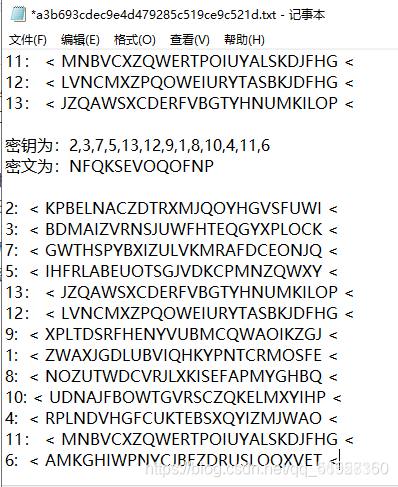
然后按照密文,将每一行进行循环移位,使得其首位字母与对应的密文相同
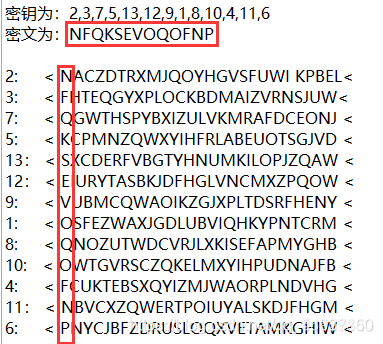
为了方便,可以把每一列的内容单独拿出来。
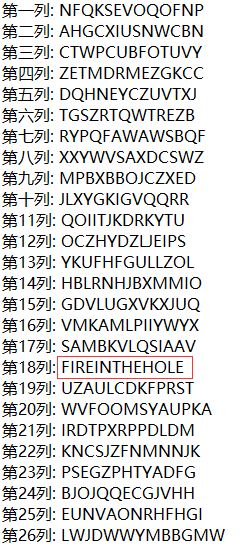
根据题目提示“二战”,只有第18列字符串“FIREINTHEHOLE”(fire in the hole–小心手雷)比较符合。
所以最终flag为: fireinthehole
easy_ECC
附件:
已知椭圆曲线加密Ep(a,b)参数为
p = 15424654874903
a = 16546484
b = 4548674875
G(6478678675,5636379357093)
私钥为
k = 546768
求公钥K(x,y)
ECC公钥的加密原理
贴一个大佬脚本
Gx = 6478678675
Gy = 5636379357093
a = 16546484
b = 4548674875
p = 15424654874903
k = 546768
x = Gx
y = Gy
for i in range(k-1):
if (x==Gx and y==Gy):
inv = pow(2*Gy, p-2,p)
temp = (3*Gx*Gx+a)*inv%p
else:
inv = pow((x-Gx), p-2,p)
temp = (y-Gy)*inv%p
xr = (temp*temp-Gx-x)%p
yr = (temp*(x-xr)-y)%p
#print(i,xr,yr)
x = xr
y = yr
print(x+y)
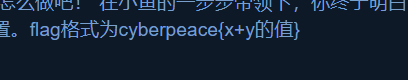
enc
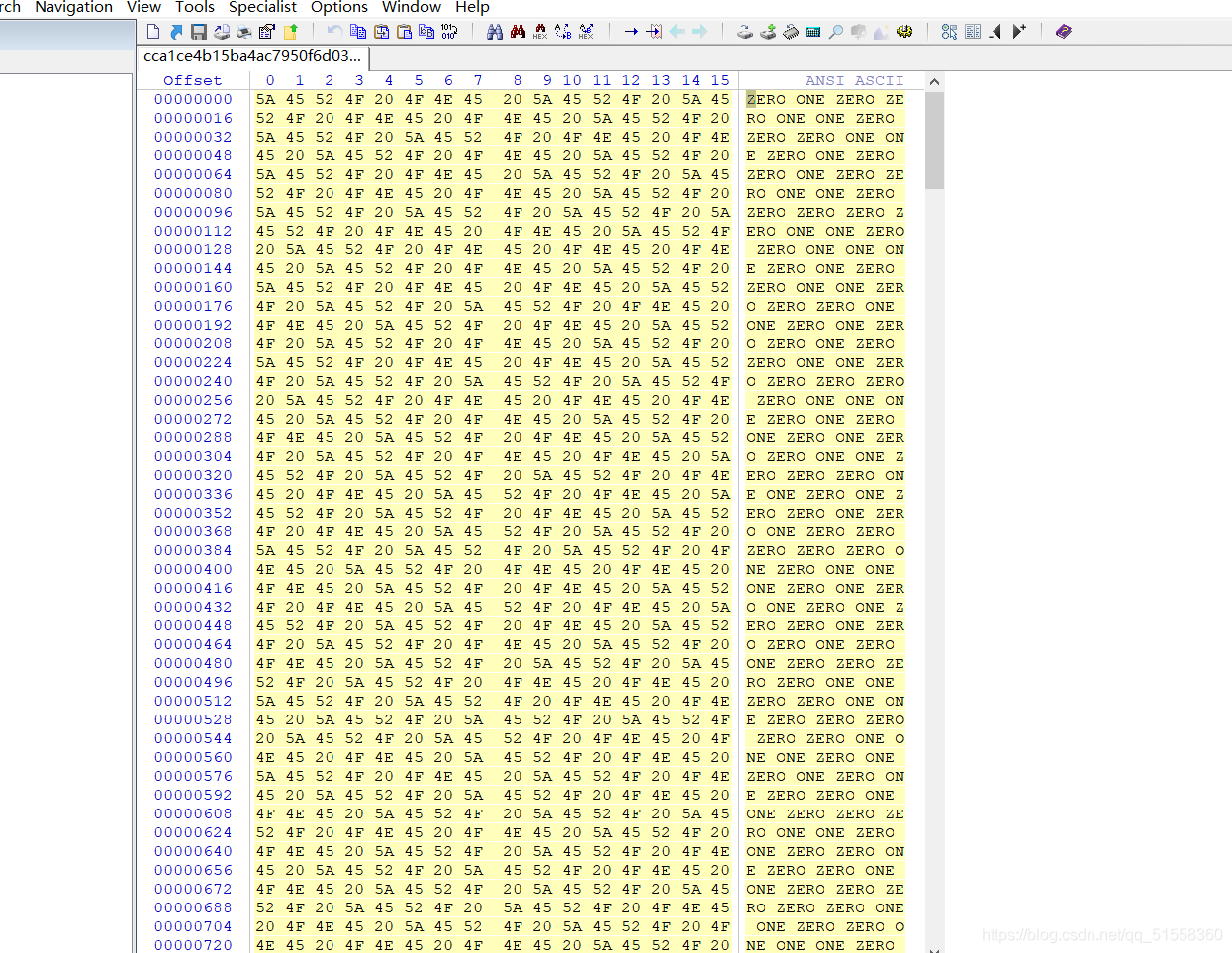
将ZERO替换为0,ONE替换为1,得:
0100110001101001001100000110011101001100011010010011000001110101010011000110100101000001011101010100100101000011001100000111010101001100011010010011000001100111010011000101001100110100011101000100110001101001010000010111010001001001010000110011010001110101010011000101001100110100011001110100110001010011010000010111010101001100011010010011010001110101010010010100001100110100011101000100110001010011001100000111010001001001010000110011010001110101010011000110100100110100011101010100100101000011001100000111010001001100010100110100000101110101010011000101001100110000011101000100110001010011010000010111010101001100011010010011010001100111010011000101001100110000011101000100100101000011001101000111010101001100011010010011010001110101010010010100001100110100011101010100110001010011010000010111010101001100010100110011000001110101010010010100001100110100011101010100110001101001001100000111010001001001010000110011010001110100010011000110100101000001011101000100110001010011001100000110011101001100011010010011010001110101010011000110100100110100011001110100110001101001010000010111010001001100011010010011000001110101010010010100001100110100011101000100110001101001010000010111010101001100011010010011010001110100010011000101001101000001011101000100100101000011001100000111010001001100010100110100000101110100010010010100001100110000011101010100110001101001001100000110011101001100010100010011110100111101
用ASCII编码得:
Li0gLi0uLiAuIC0uLi0gLS4tLiAtIC4uLS4gLSAuLi4uIC4tLS0tIC4uLi4uIC0tLSAuLS0tLSAuLi4gLS0tIC4uLi4uIC4uLSAuLS0uIC4uLi0tIC4tLiAtLS0gLi4uLi4gLiAtLi0uIC4tLiAuLi4tLSAtIC0tLSAtIC0uLi0gLQ==
看着是base64编码,解码得:
.- .-.. . -..- -.-. - ..-. - .... .---- ..... --- .---- ... --- ..... ..- .--. ...-- .-. --- ..... . -.-. .-. ...-- - --- - -..- -
进行Morse Code解码得:
ALEXCTFTH15O1SO5UP3RO5ECR3TOTXT
这里最坑的就是要自己加’{}'还有把某个字符替换成 ‘_’,尝试后获得:ALEXCTF{TH15_1S_5UP3R_5ECR3T_TXT}
fanfie
下载附件,得到如下的字符串。 长度不长,大写字母和数字组成。 很容易让人想到 Base64/32 解密。
MZYVMIWLGBL7CIJOGJQVOA3IN5BLYC3NHI
Base64 : 由 0-9、a-z、A-Z、+、/ 及后缀 “=” 组成 将任意字节序列数据编码成ASCII字符串
Base32 : 用32个可打印字符 A-Z、2-7 对任意字节数据进行编码
然而通过Base64解码并没有发现什么.
进行base32加密后得到的是:
IJEVIU2DKRDA====
与密文前面几位进行对应,发现:
MZYVMIWLGBL7CIJOGJQVOA3IN5BLYC3NHI
IJEVIU2DKRDA====
发现上面相同的字母对应的下面的字母也一致。(如 M - I 、L - D)既然如此,那便有迹可循。
因为是Base32编码。那么对A-Z、2-7 进行编码:
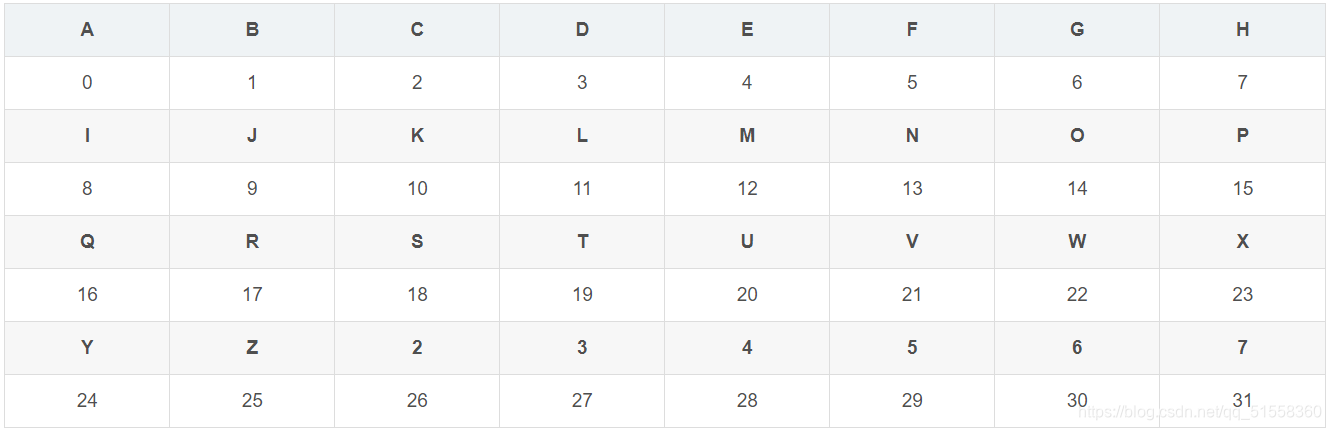
由此更直观可见,字母对应关系
3 ->11 4 ->24 8 ->12 20 ->8 21->21 25->9 26->22
这种一个字母替换一个字母的替换密码就是 仿射密码
仿射密码的a = 13和b = 4,对应表如下:
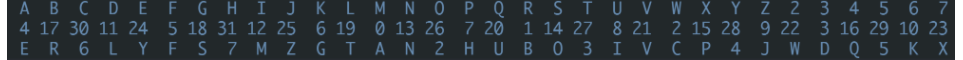
则密文进行仿射解密得:
MZYVMIWLGBL7CIJOGJQVOA3IN5BLYC3NHI -> IJEVIU2DKRDHWUZSKZ4VSMTUN5RDEWTNPU
对 IJEVIU2DKRDHWUZSKZ4VSMTUN5RDEWTNPU进行base32解密得:
BITSCTF{
S2VyY2tob2Zm}