一、简述
firewalld服务在企业7以上的版本,,是一款类似于windows界面的可以图形化设置防火墙策略的工具。
二.firewalld域
三、firewalld 的使用与安装
yum install firewalld -y ##下载firewalld服务
systemctl start firewalld ## 打开防火墙服务
systemctl enable firewalld ##开机自动启动防火墙
firewall-config ##打开图形管理界面
4.firewalld命令的使用
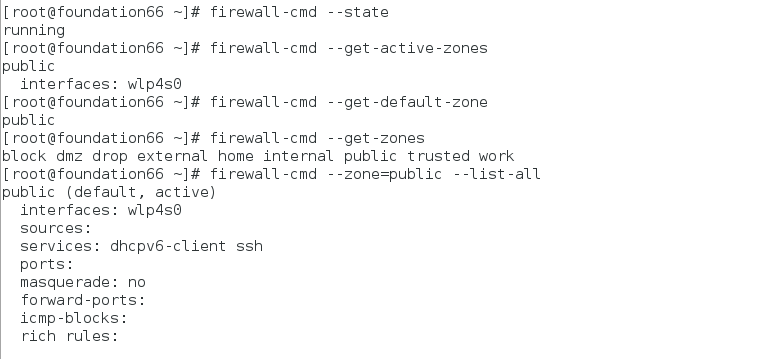
- firewall-cmd --state ##查看防火墙的状态
- firewall-cmd --get-active-zones ##查看活跃的域
- firewall-cmd --get-default-zone ##查看默认的域
- firewall-cmd --get-zones ##查看所有的域
[root@foundation66 ~]# firewall-cmd --get-services ##查看预先定义的服务
RH-Satellite-6 amanda-client bacula bacula-client dhcp dhcpv6 dhcpv6-client dns freeipa-ldap freeipa-ldaps freeipa-replication ftp high-availability http https imaps ipp ipp-client ipsec iscsi-target kerberos kpasswd ldap ldaps libvirt libvirt-tls mdns mountd ms-wbt mysql nfs ntp openvpn pmcd pmproxy pmwebapi pmwebapis pop3s postgresql proxy-dhcp radius rpc-bind rsyncd samba samba-client smtp ssh telnet tftp tftp-client transmission-client vdsm vnc-server wbem-https
[root@foundation66 ~]# firewall-cmd --list-all-zones ##查看所有域的详细情况
block
interfaces:
sources:
services:
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
dmz
interfaces:
sources:
services: ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
drop
interfaces:
sources:
services:
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
external
interfaces:
sources:
services: ssh
ports:
masquerade: yes
forward-ports:
icmp-blocks:
rich rules:
home
interfaces:
sources:
services: dhcpv6-client ipp-client mdns samba-client ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
internal
interfaces:
sources:
services: dhcpv6-client ipp-client mdns samba-client ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
public (default, active)
interfaces: wlp4s0
sources:
services: dhcpv6-client ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
trusted
interfaces:
sources:
services:
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
work
interfaces:
sources:
services: dhcpv6-client ipp-client ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
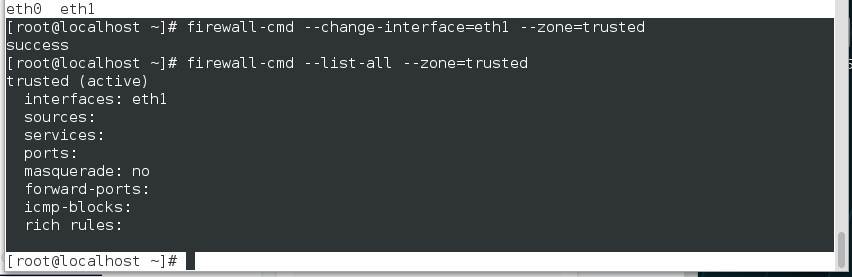
[root@foundation66 ~]# firewall-cmd --list-all --zone=trusted ##查看指定域trusted的详细信息
trusted
interfaces:
sources:
services:
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
[root@foundation66 ~]# firewall-cmd --list-all ##查看默认域的详细信息
public (default, active)
interfaces: wlp4s0
sources:
services: dhcpv6-client ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
[root@foundation66 ~]# firewall-cmd --set-default-zone=dmz ##设置默认域为dmz ,当default-zone 为public时浏览器无法访问,当为trusted时允许所有连接
success
[root@foundation66 ~]#
[root@foundation66 ~]# firewall-cmd --list-all
trusted (default, active)
interfaces: br0 wlp4s0
sources:
services:
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
[root@foundation66 ~]# firewall-cmd --list-interfaces
br0 wlp4s0
[root@foundation66 ~]# firewall-cmd --get-zone-of-interface=br0
trusted
[root@foundation66 ~]# firewall-cmd --get-zone-of-interface=wlp4s0
trusted
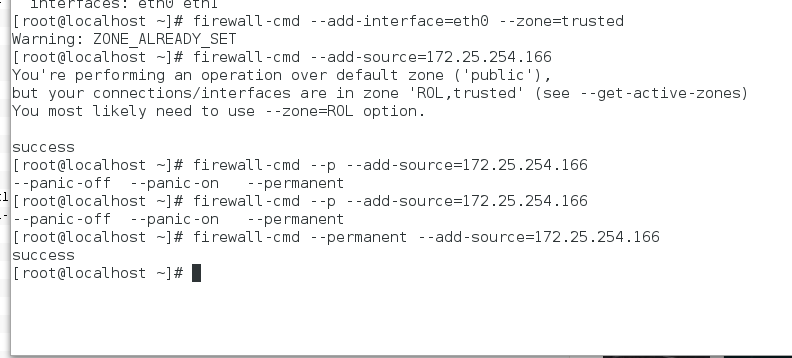
改变网卡所在的域
将public域中的网卡删除再添加到trusted上 ,所有主机就都可以访问
再将eth1 改到public域上 ,这时eth1网卡的ip就无法访问
域的永久添加
其中加上--permanent 就是永久添加
通过修改配置文件来管理
[root@localhost ~]# cd /usr/lib/fir
firewalld/ firmware/
[root@localhost ~]# cd /usr/lib/firewalld/
[root@localhost firewalld]# ls
icmptypes services zones
[root@localhost firewalld]# cd zones/
[root@localhost zones]# ls
block.xml drop.xml home.xml public.xml work.xml
dmz.xml external.xml internal.xml trusted.xml
[root@localhost zones]# vim public.xml
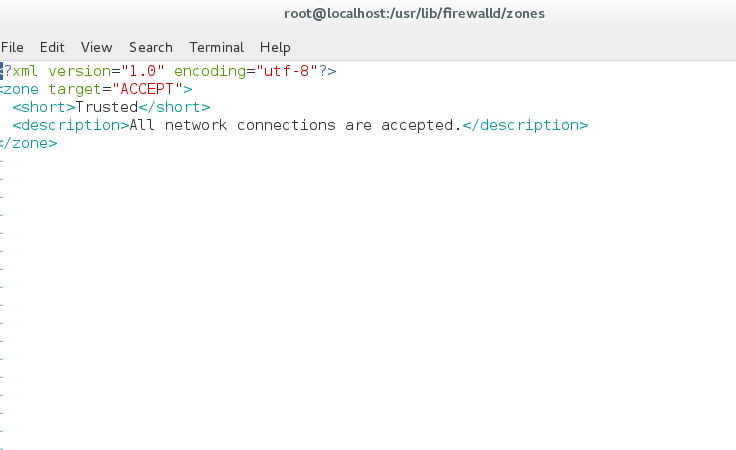
[root@localhost zones]# vim trusted.xml ##在这两个文件中就可直接添加ip地址
<?xml version="1.0" encoding="utf-8"?>
<zone>
<short>Public</short>
<description>For use in public areas. You do not trust the other computers on networks to not harm your computer. Only selected incoming connections are accepted.</description>
<source address="172.25.254.166"/> ##添加地址
<service name="dhcpv6-client"/>
<service name="ssh"/>
<service name="http"/>
</zone> 5、apache服务
首先启动httpd服务
[root@localhost zones]# systemctl start httpd
[root@localhost zones]# firewall-cmd --permanent --add-service=http
success
[root@localhost zones]# firewall-cmd --reload
success
[root@localhost zones]# firewall-cmd --list-all
这时所有的主机都可访问
[root@localhost zones]# firewall-cmd --permanent --remove-service=http
5.2基于ip的访问控制
只允许66可访问
[root@localhost zones]# firewall-cmd --direct --add-rule ipv4 filter INPUT 1 -p tcp --dport 80 -s 172.25.254.66 -j ACCEPT
success
[root@localhost zones]# firewall-cmd --direct --get-all-rules
ipv4 filter INPUT 1 -p tcp --dport 80 -s 172.25.254.66 -j ACCEPT
规则解释:在filter表里面的INPUT链添加规则 -p 协议 --dport目的地端口 -s 源 -j 方式(ACCEPT REJECT DROP)
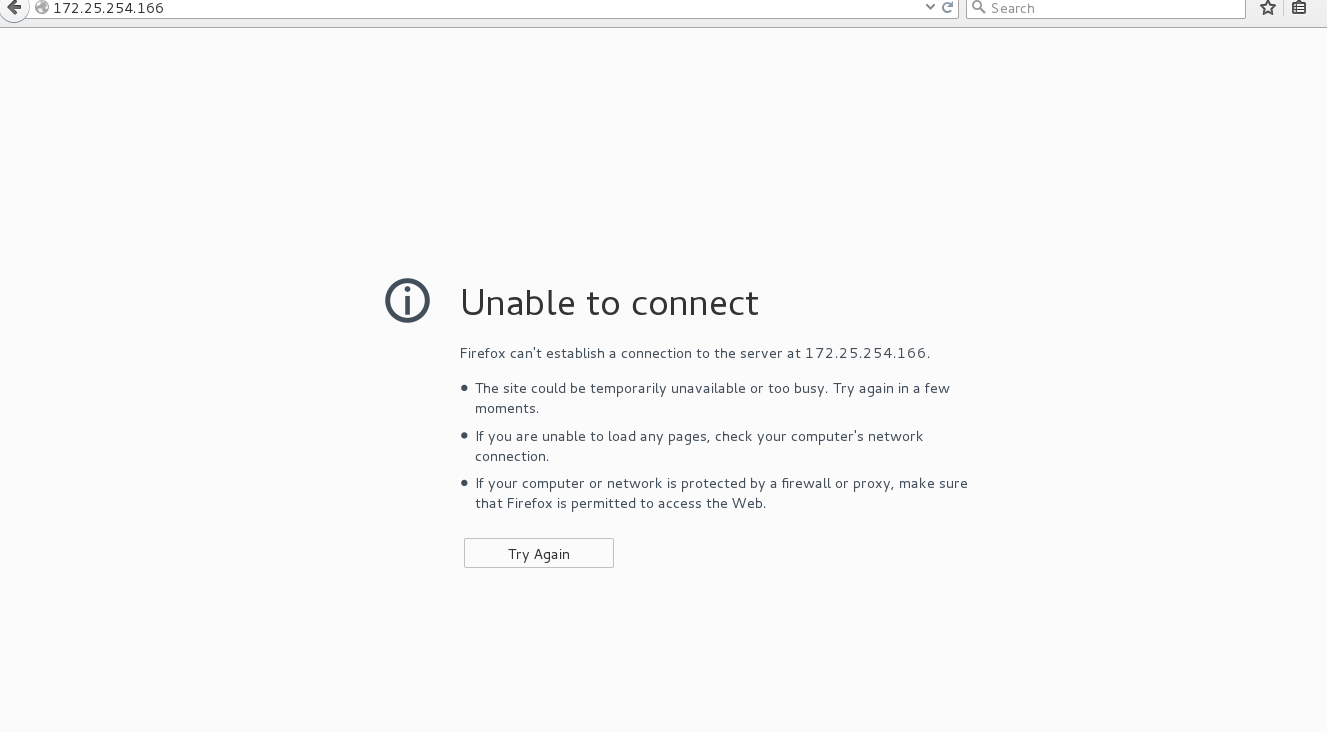
ACCEPT 表示接受;REJECT 表示直接拒绝,有反馈信息 ;DROP表示丢包,也是拒绝,但是不给反馈;对于httpd服务来说,ACCEPT表示能够看到页面,REJECT显示Unable tp connect ,DROP就会一直加载页面,但是肯定加载不出页面,也不会显示拒绝的信息。
5.3 地址伪装
添加策略
[root@localhost zones]# firewall-cmd --permanent --add-forward-port=port=22:proto=tcp:toport=22:toaddr=172.25.254.66
success
当别人通过22端口(sshd)连接我时,我把地址转换为66这个地址
[root@localhost zones]# firewall-cmd --permanent --add-forward-port=port=22:proto=tcp:toport=22:toaddr=172.25.254.66
success
[root@localhost zones]# firewall-cmd --permanent --add-masquerade
success
[root@localhost zones]# firewall-cmd --list-all
public (default, active)
interfaces: eth0
sources: 172.25.254.166
services: dhcpv6-client ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
[root@localhost zones]# firewall-cmd --reload ##!!!!需要重新家在一遍
success
[root@localhost zones]# firewall-cmd --list-all
public (default, active)
interfaces: eth0
sources: 172.25.254.166
services: dhcpv6-client http ssh
ports:
masquerade: yes
forward-ports: port=22:proto=tcp:toport=22:toaddr=172.25.254.66
icmp-blocks:
rich rules:
用ssh进行实验
- ifconfig
- eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
- inet 172.25.254.66 netmask 255.255.255.0 broadcast 172.25.254.255
- inet6 fe80::5054:ff:fe00:9c0a prefixlen 64 scopeid 0x20<link>
- ether 52:54:00:00:9c:0a txqueuelen 1000 (Ethernet)
- RX packets 2736 bytes 6447018 (6.1 MiB)
- RX errors 0 dropped 0 overruns 0 frame 0
- TX packets 2502 bytes 122174 (119.3 KiB)
- TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
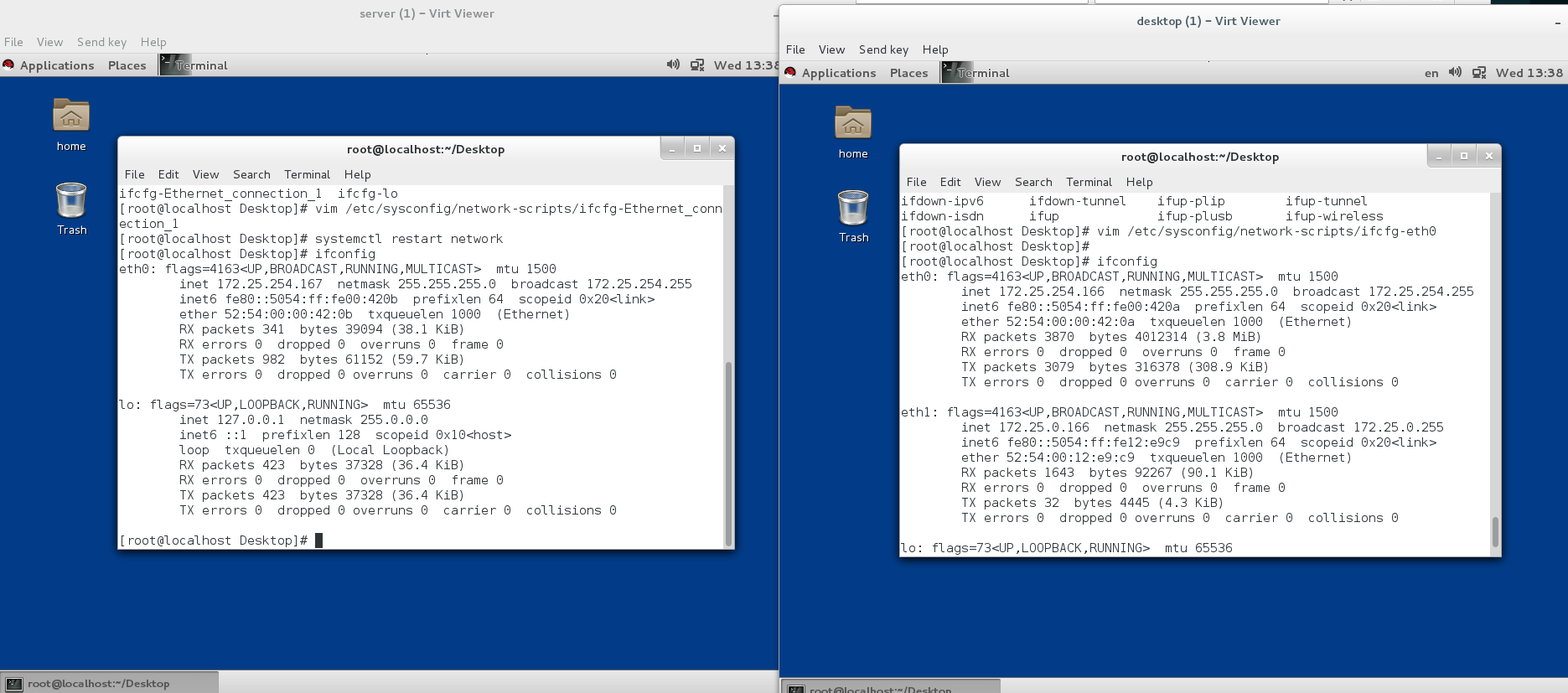
5、4实现路由功能
在服务端添加网卡配置两个ip在不同网段
[root@localhost network-scripts]# vim ifcfg-eth1
[root@localhost network-scripts]# systemctl restart network
if[root@localhost network-scripts]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.254.166 netmask 255.255.255.0 broadcast 172.25.254.255
inet6 fe80::5054:ff:fe00:420a prefixlen 64 scopeid 0x20<link>
ether 52:54:00:00:42:0a txqueuelen 1000 (Ethernet)
RX packets 3706 bytes 4004868 (3.8 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 3072 bytes 314049 (306.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.25.0.166 netmask 255.255.255.0 broadcast 172.25.0.255
inet6 fe80::5054:ff:fe12:e9c9 prefixlen 64 scopeid 0x20<link>
ether 52:54:00:12:e9:c9 txqueuelen 1000 (Ethernet)
RX packets 1481 bytes 85048 (83.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 27 bytes 3558 (3.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 0 (Local Loopback)
RX packets 600 bytes 59482 (58.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 600 bytes 59482 (58.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
成功添加两个网段
可以看到让客户端和服务端的172.25.0.166在同一个网段
也可以ping通
[root@localhost network-scripts]# firewall-cmd --permanent --remove-forward-port=port=22:proto=tcp:toport=22:toaddr=172.25.254.66
success
去掉地址伪装
[root@localhost network-scripts]# firewall-cmd --permanent --remove-forward-port=port=22:proto=tcp:toport=22:toaddr=172.25.254.66
success
[root@localhost network-scripts]# firewall-cmd --permanent --add-masquerade
success
[root@localhost network-scripts]# firewall-cmd --reload
success
[root@localhost network-scripts]# firewall-cmd --list-all
public (default, active)
interfaces: eth0 eth1
sources: 172.25.254.166
services: dhcpv6-client http ssh
ports:
masquerade: yes ##这里是yes
forward-ports:
icmp-blocks:
rich rules:
这样就可以连接不同的ip进行地址伪装