NTP反射放大攻击场景搭建
原理
攻击者冒充受害者(NTP客户端)的ip地址,向NTP服务器发送请求消息(很小),ntp服务器收到消息后向受害者返回响应数据包(很大)
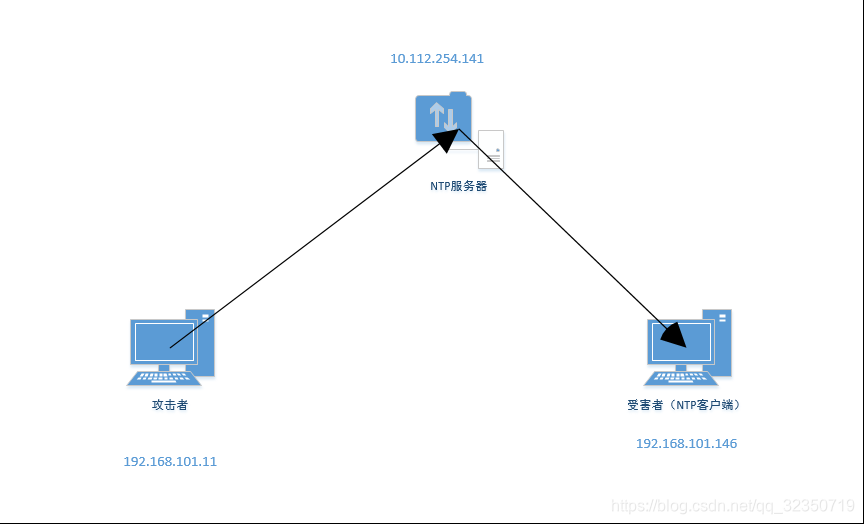
三台机器均为centos7.5
安装NTP服务器
一般情况下,选择基本的桌面版安装环境,默认是已经装了的。如果没有安装,参照下面安装步骤
yum install -y ntp- 修改/etc/ntp.conf 配置文件
# For more information about this file, see the man pages
# ntp.conf(5), ntp_acc(5), ntp_auth(5), ntp_clock(5), ntp_misc(5), ntp_mon(5).
driftfile /var/lib/ntp/drift
# Permit time synchronization with our time source, but do not
# permit the source to query or modify the service on this system.
#restrict default nomodify notrap nopeer noquery
# Permit all access over the loopback interface. This could
# be tightened as well, but to do so would effect some of
# the administrative functions.
restrict 127.0.0.1
restrict ::1
# Hosts on local network are less restricted.
#restrict 192.168.1.0 mask 255.255.255.0 nomodify notrap
# Use public servers from the pool.ntp.org project.
# Please consider joining the pool (http://www.pool.ntp.org/join.html).
server 0.centos.pool.ntp.org iburst
server 1.centos.pool.ntp.org iburst
server 2.centos.pool.ntp.org iburst
server 3.centos.pool.ntp.org iburst
#broadcast 192.168.1.255 autokey # broadcast server
#broadcastclient # broadcast client
#broadcast 224.0.1.1 autokey # multicast server
#multicastclient 224.0.1.1 # multicast client
#manycastserver 239.255.254.254 # manycast server
#manycastclient 239.255.254.254 autokey # manycast client
# Enable public key cryptography.
#crypto
includefile /etc/ntp/crypto/pw
# Key file containing the keys and key identifiers used when operating
# with symmetric key cryptography.
keys /etc/ntp/keys
# Specify the key identifiers which are trusted.
#trustedkey 4 8 42
# Specify the key identifier to use with the ntpdc utility.
#requestkey 8
# Specify the key identifier to use with the ntpq utility.
#controlkey 8
# Enable writing of statistics records.
#statistics clockstats cryptostats loopstats peerstats
# Disable the monitoring facility to prevent amplification attacks using ntpdc
# monlist command when default restrict does not include the noquery flag. See
# CVE-2013-5211 for more details.
# Note: Monitoring will not be disabled with the limited restriction flag.
注:一定要删除最后一行 disable monitor
关于对ntp.conf配置文件的说明,参照下一篇博客
- 启动ntpd服务并查看状态
启动NTP服务,并设置为开机自启动
systemctl start ntpd
chkconfig ntpd on
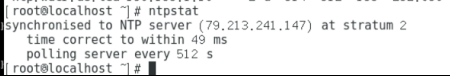
等待10-15分钟后执行 ntpstat 查看同步状态:
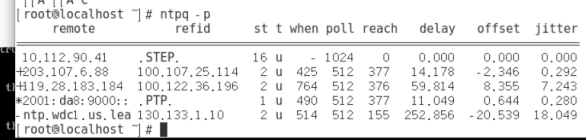
执行ntpq -p 查看与阿里云ntp服务器连接状态:
- 打开防火墙123端口
由于ntp服务使用 123端口udp协议 所以需要打开防火墙。
irewall-cmd --zone=public --add-port=123/udp --permanent
firewall-cmd --reload
安装ntp客户端
yum install -y ntp- 修改/etc/ntp.conf 配置文件
注释掉自带的
server 0.centos.pool.ntp.org iburst
server 1.centos.pool.ntp.org iburst
server 2.centos.pool.ntp.org iburst
server 3.centos.pool.ntp.org iburst
加入
server 10.112.254.141
fudge 10.112.254.141 stratum 10
ntpdc -n -c monlist 10.112.254.141
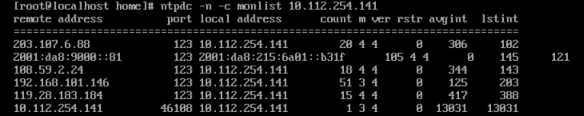
返回这样的信息即说明配置成功,并且存在漏洞