版权声明:本文为博主原创文章,未经博主允许不得转载,转载附上原文链接即可。 https://blog.csdn.net/GX_1_11_real/article/details/89681014
前言
由于前段时间,加强安全防护,需要扫描内网的弱口令的服务器,并对其修改密码。
于是写了一个基于nmap、hydra的弱密码空令检测脚本简略的脚本。
/script/Break/ip/ce_ip.txt中提供的是需要检测的ip,但是由于其中的一些服务器启用了tcp_wrapper,会导致hydra破解的时候,一直出现”[ERROR] could not connect to target port 22“,只好先用nmap对服务的版本进行查看,并将其排除,因此导致前期很缓慢。有其他好方法的,请不吝赐教。
#!/bin/bash
> /script/Break/ip/break_ip.txt
> /script/Break/log/nmap.log
for t_nmap in `cat /script/Break/ip/ce_ip.txt`
do
nmap -sV $t_nmap > /script/Break/log/nmap.log
sleep 50
echo $t_nmap
cat /script/Break/log/nmap.log |grep tcpwrap
if [ $? -eq 0 ];then
echo "$t_nmap open tcpwrap" >> /script/Break/log/tcpwrap_log.txt
echo "$t_nmap open tcpwrap"
else
echo "$t_nmap Password cracking is possible" >> /script/Break/log/tcpwrap_log.txt
echo "$t_nmap Password cracking is possible"
echo "$t_nmap" >> /script/Break/ip/break_ip.txt
fi
done
echo "Scanning is complete and the next step is started..." >> /script/Break/log/tcpwrap_log.txt
echo "Scanning is complete and the next step is started..."
>/script/Break/log/hydra_ssh.log
>/script/Break/password.txt
for hyd in `cat /script/Break/ip/break_ip.txt`
do
echo "$hyd password is being cracked"
#hydra的破解速率,可根据需求进行调整
hydra -L /script/Break/lib/userlist -P /script/Break/lib/passwdlist -vV -t 8 -e ns $hyd ssh >> /script/Break/log/hydra_ssh.log
cat /script/Break/log/hydra_ssh.log |grep "\[ssh\]" >> /script/Break/password.txt
done
echo "sucessful!"
目录结构:
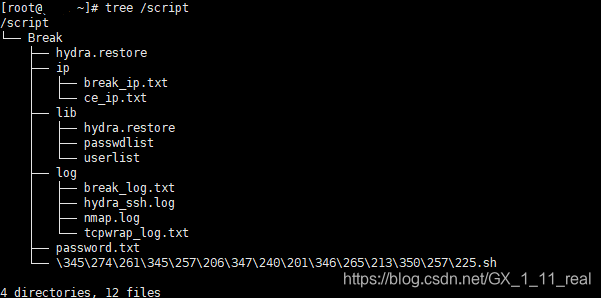
远程修改大量服务器密码脚本如下:
https://blog.csdn.net/GX_1_11_real/article/details/81167760