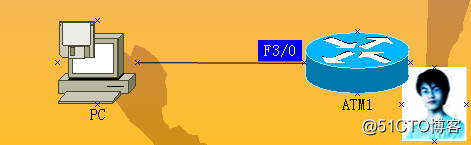
实验过程:
第一步:ATM1上的预配置
ATM1(config)#username libo password cisco
//并配置用户名和密码
ATM1(config)#int f3/0
ATM1(config-if)#pppoe enable
//开启接口的pppoe
ATM1(config-if)#no sh
第二步:配置vpdn
ATM1(config)#vpdn enable
//启用vpdn功能
ATM1(config)#vpdn-group libo
//定义vpdn的组名
ATM1(config-vpdn)#request-dialin
//请求拨号
ATM1(config-vpdn-req-in)#protocol pppoe
//开启pppoe协议,(pppoe是ppp的一种实现方式,在本质上是一种桥接式体系架构,典型的桥接实现方式存在大量的安全漏洞,在以太网桥接功能上加入ppp架构,使用pap或chap的认证可以在一定程度上解决这些问题,
ATM1(config-vpdn-req-in)#exi
第三步:配置bba-group
ATM1(config)#bba-group pppoe global
ATM1(config-bba-group)#virtual-template 1
//配置虚拟模板
ATM1(config-bba-group)#exit
第四步:配置virtual-template接口:
ATM1(config)#int virtual-template 1
//配置虚拟模板
ATM1(config-if)#ip add 10.0.0.2 255.255.255.0
//配置虚拟模板的ip地址
ATM1(config-if)#en ppp
//封装类型
ATM1(config-if)#ppp authentication pap
//认证方式。
ATM1(config-if)#peer default ip address pool libo
ATM1(config-if)#exi
ATM1(config)#ip local pool libo 10.0.0.10 10.0.0.20
//定义拨号的地址池,地址池和虚拟模板在同一个网段
第五步:拨号并查看状态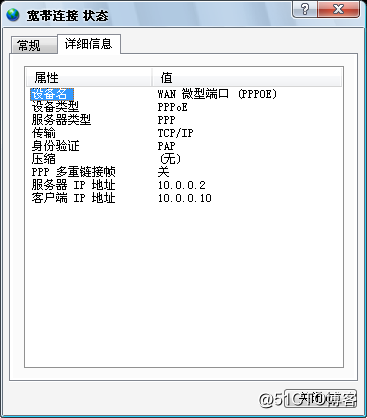
第六步:在拨号过程中,我们用wireshark进行抓包
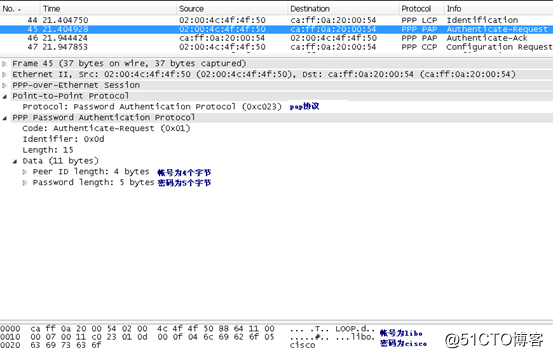
第七步:在ATM1上查看PPPoe调试信息
ATM1#sh ip local pool
Pool Begin End Free In use Blocked
libo 10.0.0.10 10.0.0.20 10 1 0
ATM1#debug pppoe events
PPPoE protocol events debugging is on
ATM1#
Jan 4 20:40:26.451: PPPoE 2: I PADT R:0200.4c4f.4f50 L:caff.0a20.0054 Fa3/0
Jan 4 20:40:26.455: [2]PPPoE 2: Destroying R:0200.4c4f.4f50 L:caff.0a20.0054 Fa3/0
Jan 4 20:40:26.459: PPPoE: Returning Vaccess Virtual-Access1.1
Jan 4 20:40:26.467: [2]PPPoE 2: AAA account stopped
ATM1#
Jan 4 20:40:32.111: PPPoE 0: I PADI R:0200.4c4f.4f50 L:ffff.ffff.ffff Fa3/0
Jan 4 20:40:32.115: Service tag: NULL Tag
Jan 4 20:40:32.119: PPPoE 0: O PADO, R:caff.0a20.0054 L:0200.4c4f.4f50 Fa3/0
Jan 4 20:40:32.119: Service tag: NULL Tag
Jan 4 20:40:32.147: PPPoE 0: I PADR R:0200.4c4f.4f50 L:caff.0a20.0054 Fa3/0
Jan 4 20:40:32.151: Service tag: NULL Tag
Jan 4 20:40:32.151: PPPoE : encap string prepared
Jan 4 20:40:32.155: [3]PPPoE 3: Access IE handle allocated
Jan 4 20:40:32.155: [3]PPPoE 3: pppoe SSS switch updated
Jan 4 20:40:32.159: [3]PPPoE 3: AAA unique ID allocated
Jan 4 20:40:32.159: [3]PPPoE 3: No AAA accounting method list
Jan 4 20:40:32.163: [3]PPPoE 3: Service request sent to SSS
Jan 4 20:40:32.167: [3]PPPoE 3: Created, Service: None R:caff.0a20.0054 L:0200.4c4f.4f50 Fa3/0
Jan 4 20:40:32.187: [3]PPPoE 3: State NAS_PORT_POLICY_INQUIRY Event MORE_KEYS
Jan 4 20:40:32.187: [3]PPPoE 3: O PADS R:0200.4c4f.4f50 L:caff.0a20.005
ATM1#4 Fa3/0
Jan 4 20:40:32.199: [3]PPPoE 3: State PPP_START Event DYN_BIND
Jan 4 20:40:32.203: [3]PPPoE 3: data path set to PPP
Jan 4 20:40:32.407: [3]PPPoE 3: State LCP_NEGOTIATION Event PPP_LOCAL
Jan 4 20:40:32.411: PPPoE 3/SB: Sent vtemplate request on base Vi1
Jan 4 20:40:32.487: [3]PPPoE 3: State VACCESS_REQUESTED Event VA_RESP
Jan 4 20:40:32.487: [3]PPPoE 3: Vi1.1 interface obtained
Jan 4 20:40:32.503: [3]PPPoE 3: State PTA_BINDING Event STAT_BIND
Jan 4 20:40:32.503: [3]PPPoE 3: data path set to Virtual Acess
Jan 4 20:40:32.507: [3]PPPoE 3: Connected PTA
ATM1#sh ip route
…………
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.0.0.10/32 is directly connected, Virtual-Access1.1
//在ATM1上可以看到PPPoE Client的路由
C 10.0.0.0/24 is directly connected, Virtual-Access1.1
ATM1#debug pppoe packets
PPPoE control packets debugging is on
//调试ppp0e数据包
Jan 4 20:44:56.951: PPPoE 3: I PADT R:0200.4c4f.4f50 L:caff.0a20.0054 Fa3/0
CA FF 0A 20 00 54 02 00 4C 4F 4F 50 88 63 11 A7
00 03 00 00
ATM1#
Jan 4 20:45:03.379: PPPoE 0: I PADI R:0200.4c4f.4f50 L:ffff.ffff.ffff Fa3/0
FF FF FF FF FF FF 02 00 4C 4F 4F 50 88 63 11 09
00 00 00 10 01 01 00 00 01 03 00 08 04 00 00 00 ...
Jan 4 20:45:03.387: PPPoE 0: O PADO, R:caff.0a20.0054 L:0200.4c4f.4f50 Fa3/0
Jan 4 20:45:03.391: Service tag: NULL Tag
02 00 4C 4F 4F 50 CA FF 0A 20 00 54 88 63 11 07
00 00 00 2C 01 01 00 00 01 03 00 08 04 00 00 00 ...
Jan 4 20:45:03.439: PPPoE 0: I PADR R:0200.4c4f.4f50 L:caff.0a20.0054 Fa3/0
CA FF 0A 20 00 54 02 00 4C 4F 4F 50 88 63 11 19
00 00 00 24 01 01 00 00 01 03 00 08 04 00 00 00 ...
Jan 4 20:45:03.459: [4]PPPoE 4: O PADS R:0200.4c4f.4f50 L:caff.0a20.0054 Fa3/0
ATM1#
02 00 4C 4F 4F 50 CA FF 0A 20 00 54 88 63 11 65
00 04 00 24 01 01 00 00 01 03 00 08 04 00 00 00 ...
ATM1#debug ppp authentication
PPP authentication debugging is on
//查看ppp认证信息。
Jan 4 20:47:31.943: ppp6 PPP: Using *** set call direction
Jan 4 20:47:31.943: ppp6 PPP: Treating connection as a callin
Jan 4 20:47:31.947: ppp6 PPP: Session handle[E4000008] Session id[6]
ATM1#
Jan 4 20:47:33.931: ppp6 PPP: Authorization required
Jan 4 20:47:34.007: ppp6 PAP: I AUTH-REQ id 12 len 15 from "libo"
Jan 4 20:47:34.007: ppp6 PAP: Authenticating peer libo
Jan 4 20:47:34.027: ppp6 PPP: Sent PAP LOGIN Request
Jan 4 20:47:34.043: ppp6 PPP: Received LOGIN Response PASS
Jan 4 20:47:34.135: Vi1.1 PPP: Sent LCP AUTHOR Request
Jan 4 20:47:34.139: Vi1.1 PPP: Sent IPCP AUTHOR Request
Jan 4 20:47:34.151: Vi1.1 LCP: Received AAA AUTHOR Response PASS
Jan 4 20:47:34.155: Vi1.1 IPCP: Received AAA AUTHOR Response PASS
Jan 4 20:47:34.159: Vi1.1 PAP: O AUTH-ACK id 12 len 5
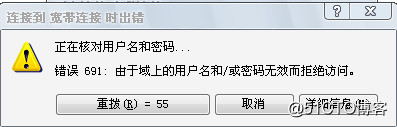
问题分析:
出现PADT的情况:
如果在电脑上输入的用户名或者密码有误,则路由器上会出现上列padt的接口
May 10 13:58:11.263: PPPoE 3: I PADT R:0200.4c4f.4f50 L:caff.0bc8.0054 Fa3/0
在pc上会出现下列情况(691错误)